How to create Sophos Firewall Bypass Rule
You can disable the Web filter, Intrusion prevention, Application Control, Advanced Threat Protection or other security features on the firewall. But the traffic still passes through the packet filter. To actually disable everything, there is a bypass rule. When this is enabled for a host or network, the traffic is affected by the firewall.
Commands for Bypass Rule
Connect to the firewall via SSH to start the Device Console. After that you need the following commands.
Create Bypass Rule
In our example we want to create a rule from network 192.168.33.0/24 to network 192.168.46.0/24.
set advanced-firewall bypass-stateful-firewall-config add source_network 192.168.33.0 source_netmask 255.255.255.0 dest_network 192.168.46.0 dest_netmask 255.255.255.0The back rule must not be missing either. That the traffic from the destination network also goes through the bypass rule against our firewall.
set advanced-firewall bypass-stateful-firewall-config add source_network 192.168.46.0 source_netmask 255.255.255.0 dest_network 192.168.33.0 dest_netmask 255.255.255.0
⚠️ The bypass rule lets everything through, so you no longer need firewall rules and the traffic is no longer displayed in LogViewer. You should really only create a rule if you know what you are doing and are aware of the security risk. The firewall will simply let the traffic through and none of the protection functions will work for the specified network anymore.
Show rules
The following command can be used to display which bypass rules are recorded on the firewall.
show advanced-firewall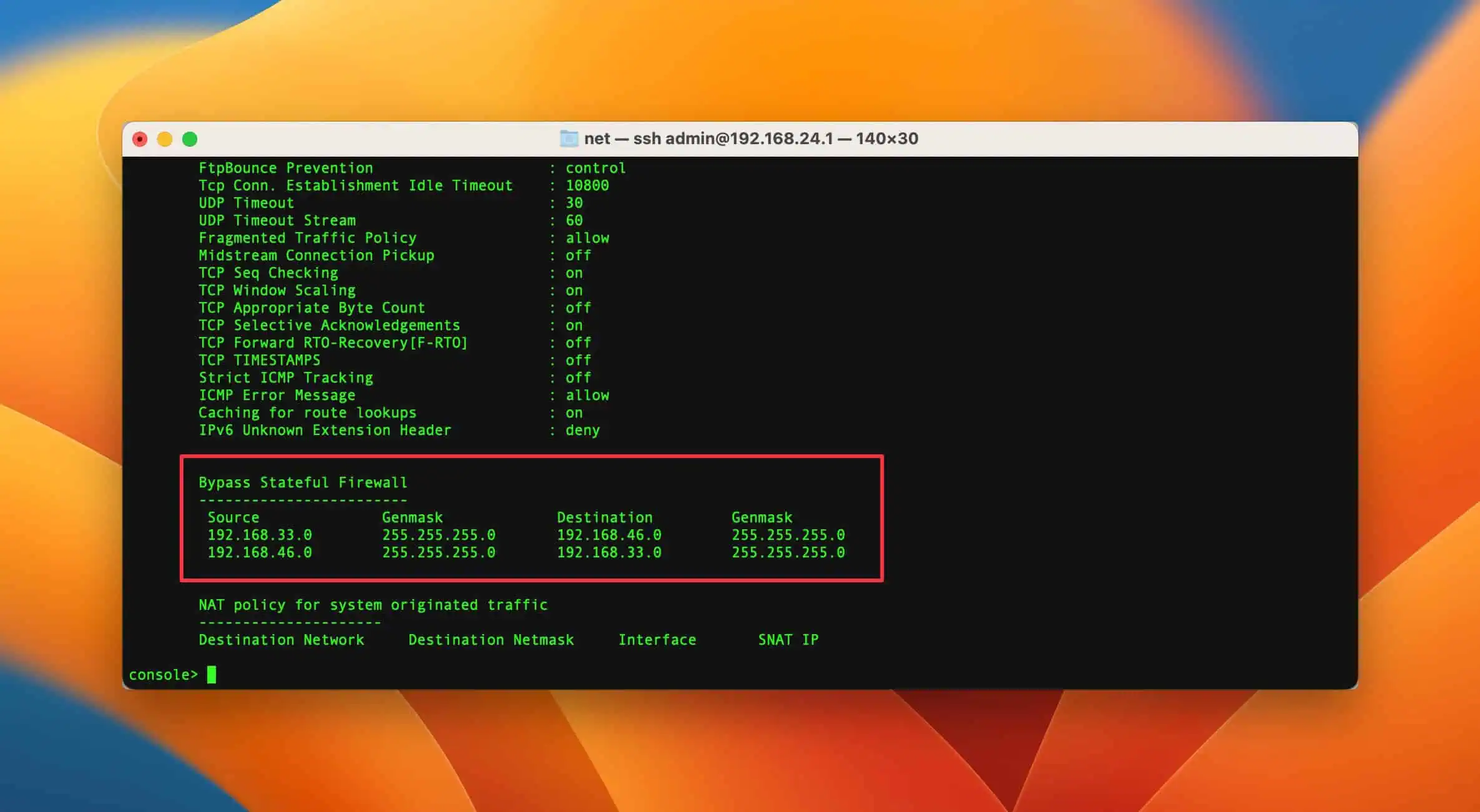
Delete Bypass Rule
The delete command almost identical to the command to create the rule. Instead of add, one uses del.
set advanced-firewall bypass-stateful-firewall-config del source_network 192.168.33.0 source_netmask 255.255.255.0 dest_network 192.168.46.0 dest_netmask 255.255.255.0