How to document Sophos Firewall rule easily
In this article I explain how to document a firewall rule at least a little better with minimal effort.
Probably only very few of us have the time to document everything properly. If you do succeed in creating documentation, it is often poorly maintained and you change something on the firewall and then forget to document it.
When you do a security audit, terms like “change management process” come up and remind you what you don’t have time for or that other tasks have a higher priority.
Firewall rules describe
Experience shows that the number of firewall rules tends to increase over time rather than decrease. Often you can only vaguely remember why individual rules are there or what they do. Simply deactivating them when traffic is still going through works, of course. As a rule, you can then very quickly hear what they were used for. But this is not the most elegant way and certainly not possible everywhere.
I recommend that as a minimum, when creating or editing firewall rules, you take 60 seconds to describe the firewall rules.
To do this, you do not even have to open an external document, but can do this right in the firewall itself.
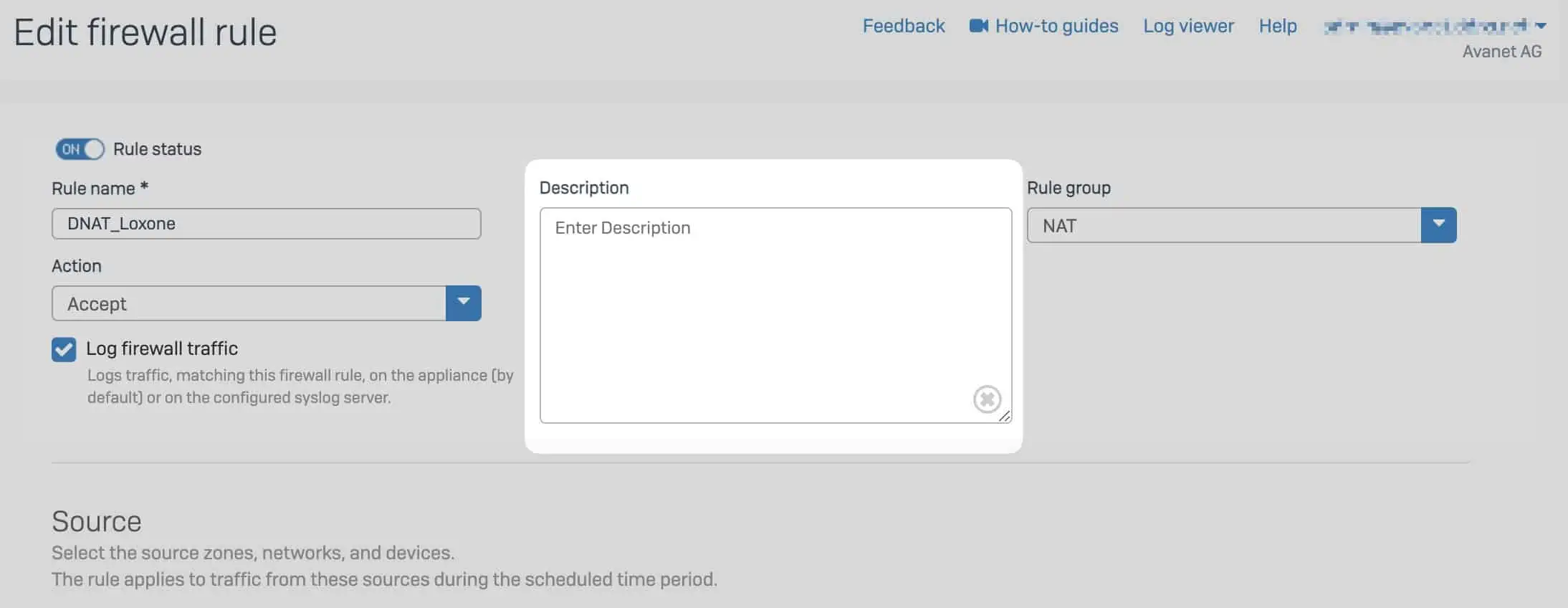
You have 255 characters, almost as much as a tweet (280), with which you can change the world. So there should be enough to explain what the firewall rule does.
Example for describing a firewall rule
Of course, it is completely up to you what you write in this field. Here are a few ideas of what might be helpful in the future:
- NAME: What does this rule do – why was it created or for what application is it needed?
- AUTHOR: Who created the rule?
- LAST MODIFIED: When was the rule created or last changed and from. To save characters here, work with the initials or user names.
- COMMENT: e.g. for a telephone number, contact person of the partner company that maintains the software or by which department or person this rule is used.
- DOC: You can shorten URLs for online documentation or instructions or store a file name with which you can search on the internal drive.
5G Access - Smarthome
---
AUTHOR: Patrizio
LAST MODIFIED: 12.12.2012 [PP]
COMMENT: Just for Tonys iPhone
DOC: bit.ly/3Nmn3lXRemember. The firewall rule itself contains a lot of information such as IPs and ports. So you don’t have to write everything in the text field that is defined in the rule anyway. But everything is helpful in the future to understand why the rule was created.