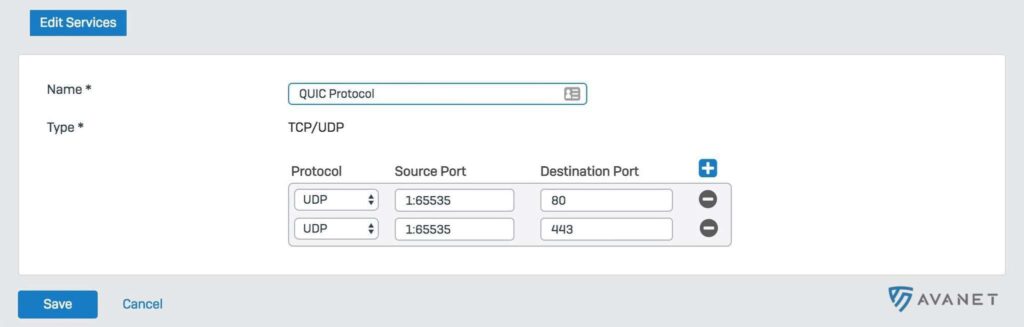
Sophos Firewall and the QUIC protocol
In this article we will explain what the QUIC protocol is and why you should disable it for security reasons, at least for now.
What exactly is the QUIC protocol?
QUIC stands for “Quick UDP Internet Connections” and was developed by Google to make the Internet faster.
Let’s take a well-tried protocol, such as HTTP (Hyper Text Transfer Protocol). This already exists in a second version – HTTP/2. The transport protocol that HTTP relies on is TCP. This has proven to be reliable, but it is also not exactly fast. The connection takes a long time to establish and if the page is then also encrypted with SSL, i.e. HTTPS, it takes even longer. This is exactly where Google came in and created QUIC, a protocol that is not only secure, but also enables fast connections.
QUIC does not use TCP, but UDP, which is faster but also less reliable. Because of its speed, the protocol is therefore also often used for video or audio streaming. With QUIC, Google has managed to compensate for the unreliability of UDP and thus develop a fast, stable and secure protocol.
The web server running this website here already supports QUIC. HTTP/2 is used as the protocol by default. However, if you are using Google Chrome, QUIC is used. On the following screenshot you can see how the whole thing works. Massively less packet turnaround time (Round Trip Time > RTT).
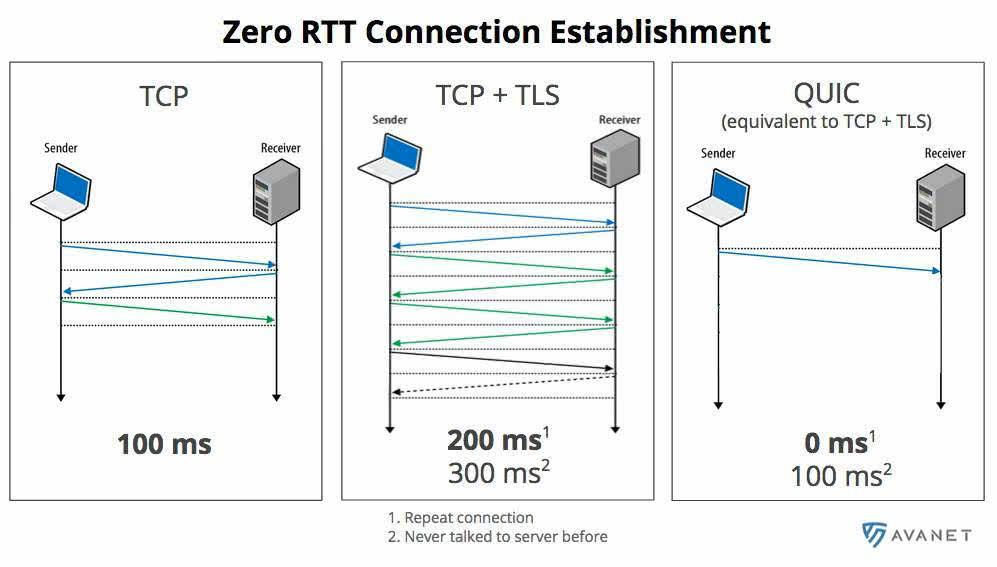
But QUIC can do more, such as maintaining the connection to the web server. You are probably familiar with the behavior that when you visit a website at home and then want to view it again later on the road via 4G or in the office via the WLAN, the page is reloaded. This behavior is triggered because your IP address has changed, causing you to disconnect from the web server. With QUIC this won’t happen to you, because it works with browser detection and the connection can be easily re-established.
QUIC – Uncontrollable with Sophos at the moment
Google has definitely developed something great with QUIC and with almost 60% market share of the Google Chrome browser (source: statista), they definitely have the power to spread this protocol.
The problem, however, is that QUIC bypasses WebProxy, Sophos Sandstorm, and also malware scanning and content filtering. The reason for this is that currently only HTTP and HTTPS can be scanned by the web filter. So, as with HTTPS scanning, the firewall owner must take action to avoid taking any risks.
Disable QUIC
1st option: Via Google Chrome
The first option would be to disable the QUIC protocol directly in the Google Chrome browser. To do this, simply enter chrome://flags/ in the address bar and deactivate QUIC.

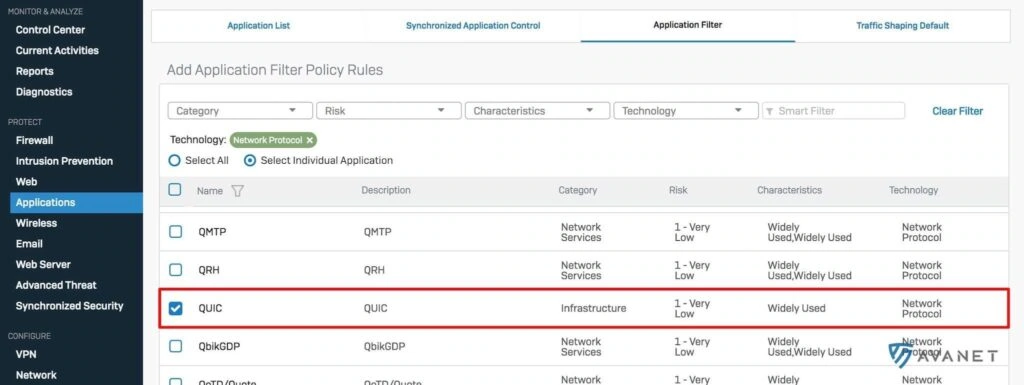
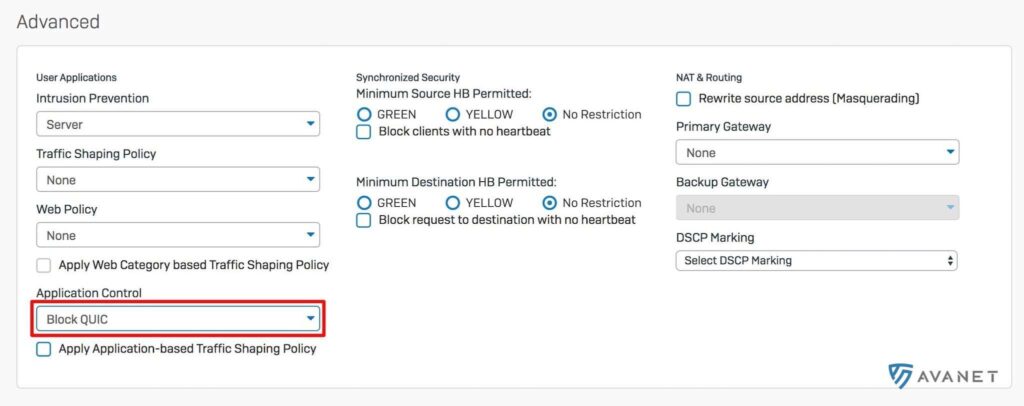
2nd option: Via Application Control
If you prefer to block QUIC via the firewall, you can control this via Application Control. Simply create a new filter, add the QUIC protocol and finally select the created filter under Application Control.
3rd option: block UDP on the firewall
The third option is to simply block UDP on ports 443 and 80 on the firewall, which will then automatically use HTTP/HTTPS.