Sophos Central Update – Enhanced protection for servers and more
Over the last two months, Sophos has again released a few innovations for the Central platform, which I would like to briefly summarize here. I will start this article, however, with a note about the imminent end of support for Windows 7 and Server 2008 R2.
Soon end of support for Windows 7 and Windows Server 2008 R2
Microsoft has now finally discontinued support for both Windows 7 and Windows Server 2008 R2 on January 14, 2020. As a result, Sophos will no longer support these two operating systems for much longer. Standard support officially ends on December 31, 2021.
Windows 7
- End of standard support: December 31, 2021
- End of extended support: March 31, 2025
Windows Server 2008 R2
- End of standard support: December 31, 2021
- End of extended support: March 31, 2025
Info: Windows Server 2008 support ends on July 31, 2020.
Acquire an extended support
Sophos is offering extended support to customers who do not have a December 31, 2021 deadline to replace existing hardware. You will need to purchase an extra license for Sophos to give you a grace period until March 31, 2025 for the following products:
- Intercept X Advanced/Intercept X Advanced with EDR
- Intercept X Advanced for Server/Intercept X Advanced for Server with EDR
- Central Endpoint Protection/Central Server Protection
- Endpoint Protection Standard/Endpoint Protection Advanced
- Server Protection for Virtualization, Windows and Linux/Server Protection Enterprise
If you are interested in such an extended support, just write us via contact form. We will be happy to provide you with an appropriate offer.
Sophos Intercept X Enhanced Protection (Beta) now available for servers
Sophos has already launched a beta program for Intercept X Enhanced Protection in October 2019. The goal of this program is to further drill down Intercept X and provide new functionality to combat current malware. Even in 2020, ransomware attacks are not stopping and terms like EMOTET are on everyone’s lips. Sophos therefore continues to work diligently to ensure that customers can continue to feel secure with Intercept X technology.
In the first version, Intercept X Enhanced Protection already included the two functions Anti-Malware Scanning Interface (AMSI) and Intrusion Prevention System (IPS).
In December 2019, new and very important protection mechanisms for Windows systems were added, which are now also available for Windows Server from version 2008 R2:
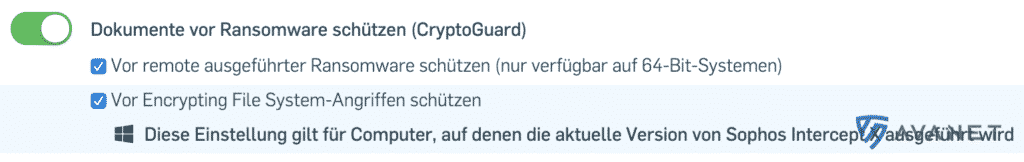
Protection against encryption file system attacks (EFS Guard)
Since Windows 2000, Microsoft has integrated a function called EFS (Encrypting File System) into its operating system. Not to be confused with BitLocker, which can be used to encrypt an entire hard drive, EFS is used to encrypt specific files and folders.
Attackers have found a way to abuse this function and encrypt their victims’ data right away using the APIs of the system’s own encryption function (EFS). What is practical about the whole thing is that they do not have to reload their own malware for it. With EFS Guard, Intercept X can now protect against such attacks.
Dynamic shellcode protection
The inventors of new malware are increasingly using so-called “stagers”. This refers to small and innocent programs that download and execute malware in the temporary memory. As a result, they are hardly detected by traditional anti-malware applications. By analyzing the behavior of applications, dynamic shellcode protection can protect against exactly such malware. When behavior similar to that of a stager is detected, the detection immediately intervenes and stops the application.

Validate CTF Protocol Caller (CTF Guard)
CTF is a vulnerability in a Windows component that has been present since Windows XP. This vulnerability allows an unauthorized attacker to control any Windows process, including applications running in a sandbox. To ensure that the CTF protocol can no longer be exploited, the Sophos Threat Mitigation team has developed the CTF Guard feature and added it to the Threat Protection policy.

Prevent side-loading of unsafe modules (ApiSetGuard)
The ApiSetGuard function prevents applications from loading a malicious DLL masquerading as an ApiSet stub DLL. ApiSet Stub DLLs are DLLs that help a program to be compatible with newer Windows versions. Attackers can deposit malicious ApiSet stub DLLs on a system to manipulate functions. For example, the Sophos tamper protection could be overridden to terminate the Sophos client.

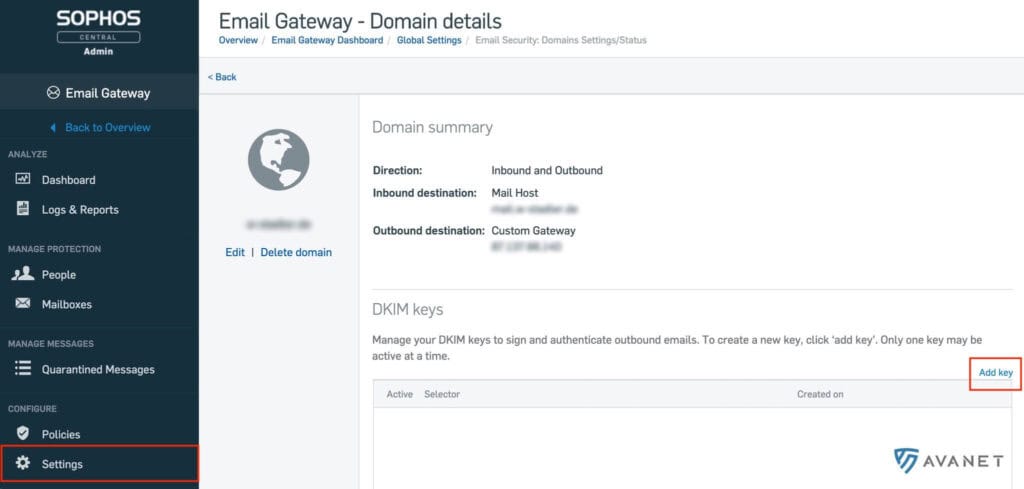
E-mail DKIM signing
Those who use Sophos Central Email to scan their inbound and outbound traffic can now add a DKIM signature to their emails. To set this up, you need to go to the “Settings” of Central Email and select the “Domain Settings/Status” menu item. If you now click on a domain that also scans outbound traffic, you will find the option to create a new DKIM key below the summary. Subsequently, a short instruction appears with all necessary information to set up the DKIM key.
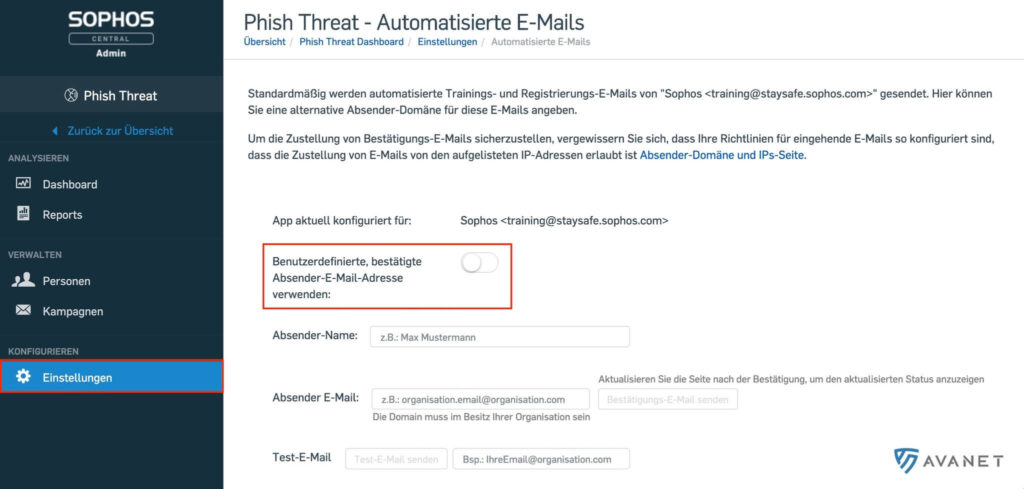
Customizable email address for Phish Threat Training
Sophos Centrla Phish Threat is actually designed to train employees in a company to detect phishing emails. In the past, it was not really trustworthy when the automated training and registration emails were sent by “Sophos training@staysafe.sophos.com”. Many an unsure employee has probably asked himself whether he should really click on the link in this e-mail. 😅 Sophos has now reacted to this and now offers the option to store your own domain for catch emails, reminder emails and registration emails that are sent to your end users.
To do this, simply go to the “Settings” of Phish Threat and select the menu item “Training notification and reminder emails”. A custom email address can now be activated and confirmed there. In my tests, however, the verification email, as well as the subsequent test email, ended up in the spam folder. By the way, these settings are applied to the Central Account and cannot be set individually per campaign.