
Sophos Zero Trust Network Access – An alternative to VPN
Sophos recently released the public beta for its new Sophos Zero Trust Network Access (ZTNA) product. Anyone can register now for the ZTNA Early Access Program. Let’s take a look at what the Zero Trust security model is and what makes it one of the most secure cybersecurity frameworks in the world.
What is the Zero Trust model?
The zero trust model simply states that an organization must not trust all requests to access data and the source must always be verified first. To put it in three words: Trust no one. Do not give anyone access to your network unless you know 100% who wants to access your data and agree to it.
But why use this exaggerated and almost paranoid security model? Well, let’s consider that Cybersecurity Ventures have predicted that cybercrime will cause $6 trillion in damage worldwide by 2021. This is the expected loss despite costly investments in cybersecurity by some of the world’s largest companies. No one is safe from cyber attacks, SQL injections and illegal access.
The Zero Trust model proposes to change the concept that organizations focus on threats from the outside, while assuming that anything already on the inside does not need authorization and is harmless. Most security breaches occur because it is easy for hackers to gain access to more information within the system once access has been granted. Before you put all your faith in the Zero Trust model, let’s take a look at the pros and cons of this framework.
Advantages of the Zero Trust Model:
- The company is much less vulnerable to cyber threats.
- The authentication procedures are very strict.
- Improved protection of corporate data.
- Very sophisticated security structure.
Disadvantages of the Zero Trust model:
- Requires a lot of time to set up.
- Managing a large number of users is very time-consuming, as all access requests must be authenticated.
- More difficult to back up data because data is stored in multiple locations
What is ZTNA?
ZTNA is the latest product from Sophos Central, deployed and managed entirely in the cloud. Its purpose is to provide remote users with secure application access. What is ZTNA about? It is based on the Zero Trust framework, which means that the user is verified in every possible way to minimize the likelihood of compromise. This includes user authentication (typically two-factor authentication to ensure that stolen credentials do not lead to misuse), validation of device health, and verification of the device’s compliance status to decide whether to grant access.
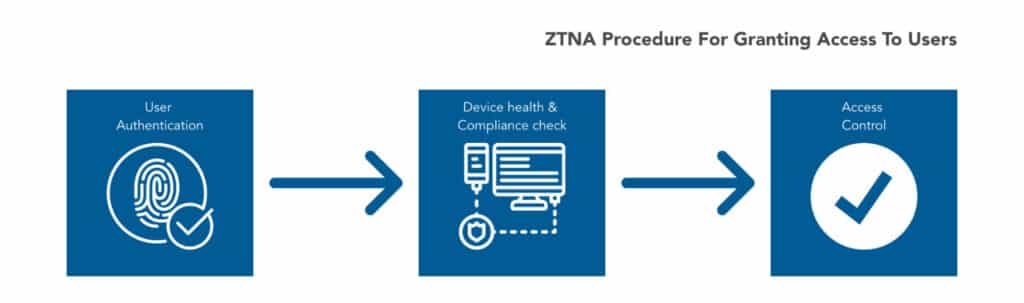
How does ZTNA compare to VPN?
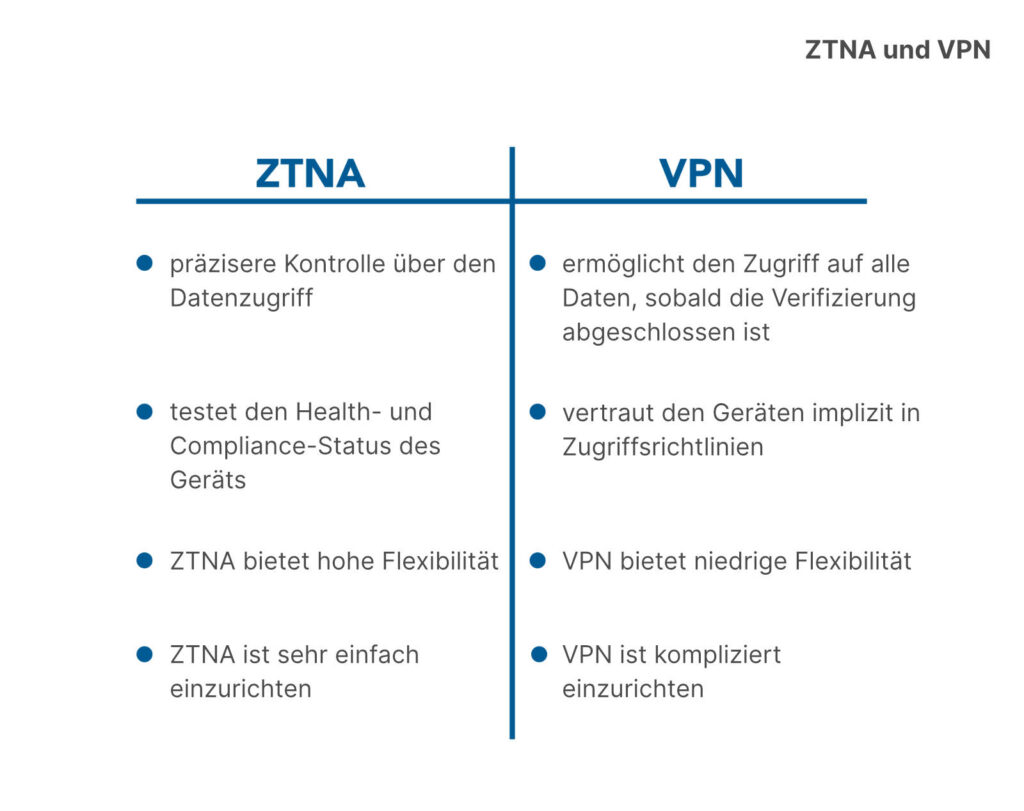
While VPN was a good option for us, ZTNA offers a better solution when we set them against each other. How does ZTNA outperform VPN?
- Better security: The security of the networked application will improve dramatically because, unlike VPN, ZTNA will also verify the integrity and status of the device. Faulty equipment can cause serious damage to other equipment.
- Transparent: ZTNA offers users high transparency with smooth connection management. VPN can be difficult and prone to initiating support calls.
- Granular control: ZTNA provides segmented access to the application’s data, unlike VPN, which allows the user to access all data once verification has gone through. Attackers love this because once inside, they have unlimited time to move from device to device. Once authenticated, that could mean access to thousands of devices.
Since VPN is a technology that was developed over 20 years ago, it is a bit outdated. It was created with the goal of extending trusted networks to connect enterprise employees in a unified network. But now cloud-based applications have a large number of users connecting to them across multiple devices, making VPN a vulnerable and insecure choice. Hackers exploit these vulnerabilities all the time, making VPN vulnerabilities a serious threat to businesses.
What applications can ZTNA protect?
ZTNA protects all networked applications hosted on on-premises networks or available in the public cloud. This includes applications like Wiki or Jira or any other kind of repositories or ticketing apps. ZTNA does not provide protection for applications that are not owned by the customer.
Components of ZTNA
There are three different components for Sophos ZTNA:
- Sophos Central: provides a cloud management platform for all Sophos products, including Sophos ZTNA, which is cloud-ready and enables easy deployment, policy management and reporting.
- Sophos ZTNA Gateway: a virtual appliance for protecting on-premise or public cloud-networked applications with initial support for AWS and VMware ESXi, and will soon support Azure, Hyper-V and Nutanix.
- Sophos ZTNA Client: provides seamless connectivity to applications based on end-user identification and device state. It is easy to implement and receives device status from Windows Security Center. Initially, it will only support Windows, with support for macOS, Linux, and the iOS and Android mobile operating systems to follow shortly.
When can Sophos ZTNA be used?
Sophos is proud to announce that they have already begun the Early Access Program for Sophos Zero Trust Network Access (ZTNA). The first phase will enable clientless access to browser applications such as CRM and ticketing applications (JIRA). The next phase will include further enhancements such as Windows client support with integrated deployment alongside Intercept X, Synchronized Security for Device Health, additional Identity Providers and a gateway for AWS.
Licensing and pricing
As we already know from other Central products, ZTNA is licensed per user and not per device. So a user with multiple devices needs only one license. There will also be a free trial version at launch, so users can take a look under the hood before deciding to purchase the license.


