Sophos Firewall Troubleshooting – Tips & Tricks for the CLI
As an IT administrator responsible for managing Sophos Firewall, an in-depth knowledge of the Command Line Interface (CLI) is essential. The CLI provides powerful tools and commands that not only allow you to efficiently navigate through the system directories, but also perform detailed analysis and troubleshooting. In this article, we’ll show you how to make the most of Sophos Firewall’s CLI to browse logs, monitor network connections, securely transfer files and start services in debug mode. This guide will help you to understand the most important commands and use them in your daily work.
Topics
Navigating in the Sophos shell
In the Sophos Shell, you can search the directory structure using simple Linux commands.
For example, to display the existing log files in the /log directory, you can use the following command:
cd /log
ls -la- cd /log: Changes to the /log directory where the Sophos Firewall log files are located.
- ls -la: Lists all files in the current directory in detail, including hidden files. The -l shows detailed information such as file size and timestamp, while -a lists all files including the hidden ones.
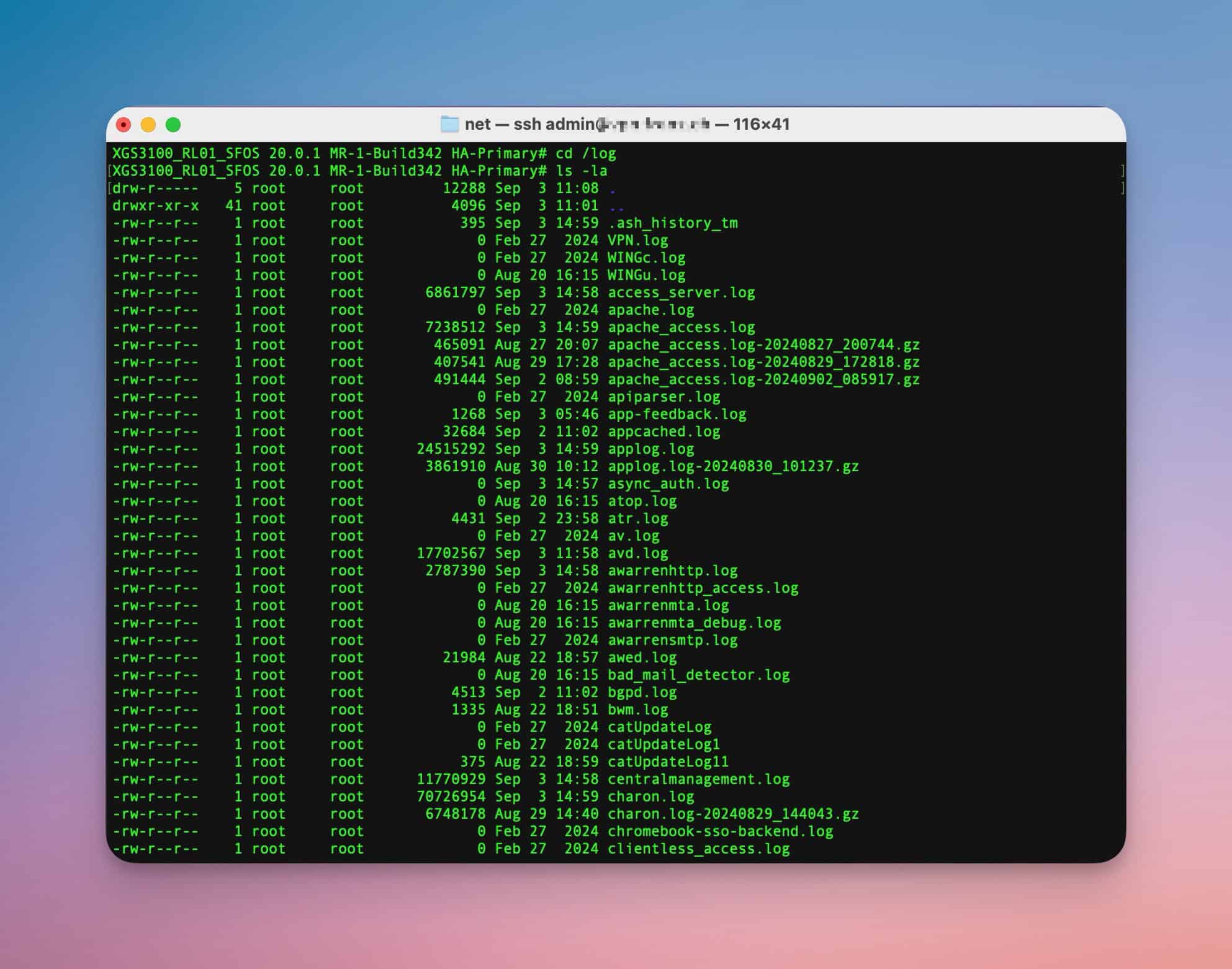
To display the files sorted by size, you can extend the ls command as follows:
ls -lSrh- -lSrh: These options list the files in detailed form, sorted by size (-S) and in a readable form (-h for “human-readable”).
Display and search logs
Searching and analyzing log files is one of the most common troubleshooting tasks. The cat, tail and grep commands are extremely useful for this.
tail – monitor log in real time
To track the contents of a log file in real time, you can use the tail command:
tail -f smtpd_main.log- tail -f: Displays the last lines of the smtpd_main.log file and updates it in real time when new entries are added.
grep – Filter logs
To search for a specific term, e.g. a domain or e-mail address, in a log file, you can use grep:
cat smtpd_main.log | grep "avanet.com"Or you want to monitor the IPsec log in real time and display entries for an IP address
tail -f strongswan.log | grep 46.33.21.12- grep: Searches the smtpd_main.log file for lines containing the term “avanet.com”.
Other useful options for grep:
- -i: Ignores upper and lower case when searching.
- -n: Displays the line numbers of the hits.
- -m 1: Ends the search after the first hit.
Conntrack and TCP Dump
Sophos Firewall provides powerful tools for analyzing network connections and traffic.
Conntrack
With conntrack you can monitor active connections:
conntrack -L | grep "10.128.138.150"- conntrack -L: Lists all active connections on the firewall.
- grep “IP address”: Filters the connections associated with the specified IP address.
tcpdump
To analyze network traffic directly, you can use tcpdump:
tcpdump -i any port 80- tcpdump -i any: Monitors all network traffic on all interfaces.
- port 80: Filters the traffic that runs via port 80 (HTTP).
The topic tcpdump is covered in a separate article, as it is very extensive: Sophos Firewall – collecting logs with TCPDump for analysis
Download and upload files
To download files from the firewall, you can use tools such as WinSCP or, on macOS, Cyberduck. You must first ensure that SSH access to the firewall is permitted. Then, of course, you cannot connect to the tool and transfer files easily.
You can use ftpput to upload files to an FTP server:
ftpput -u username -p password ftp.server.com /path/to/upload/file.logftpput -u sophostransfer@avanet.com -p UrXPMmGYXtAsaX6?LnAJx3fgrK www.avanet.com strongswan.log- ftpput: Transfers a file to an FTP Server.
- -u username -p password: Authenticates with the specified FTP login data.
- ftp.server.com: Address of the FTP Server.
- /path/to/upload/file.log: Path to the local file to be uploaded.
Alternatively, you can also use the curl command to upload files to an FTP:
curl --ftp-ssl ftp://www.avanet.com -u sophostransfer@avanet.com:Ur$tAs3fg46rK -v -T {/tmp/ips.log,/tmp/applog.log,/tmp/csc.log,/tmp/u2d.log}List of all firewall services and their logs
Sophos has an excellent list of all services and the corresponding logs: Sophos KB: Log file details.
List firewall services
This Advanced Shell command lists all active services and their status:
service -SOr you only need the status of a single service. The status of a service can also be checked with service -S in combination with grep:
service -S | grep strongswanHowever, this command does the same on the Firewall Console:
system diagnostics show subsystem-info Debug log
Debug mode is essential when normal logs do not provide enough information to understand a problem. Compared to normal log mode, which only records basic events and error messages, debug mode provides deeper, more detailed logging. It captures more comprehensive data and internal processes that are not visible during normal operation. This makes it possible to precisely identify complex or rare errors, which is particularly helpful when diagnosing problems that could be overlooked in normal log mode.
To start a specific service in debug mode, you can use the following command:
service ips:debug -ds nosyncTo end the debug mode again so that the log cannot fill the hard disk, you should deactivate it again after some time:
service ips:debug -ds nosync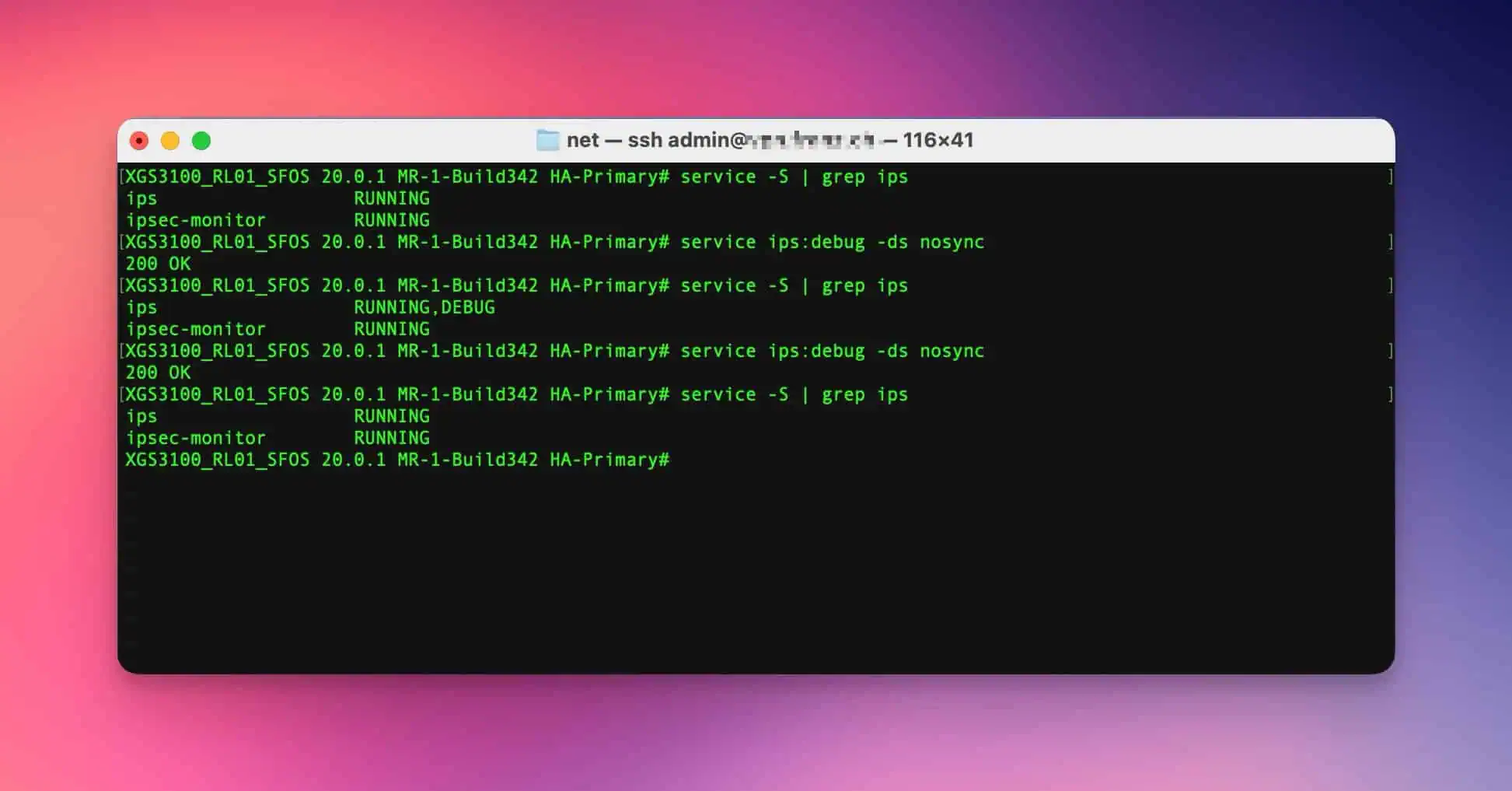
We have described the topic of services and restarting in more detail in this article: Restarting Sophos Firewall services
Last words
Navigating and working on the Sophos shell may seem complex at first, but with the right commands you can identify and fix problems quickly and efficiently. This guide is designed to help you understand and use the most important commands effectively. A solid knowledge of the CLI can significantly improve your ability to solve problems, alternatively our support is of course also available.