Understanding Sophos Firewall performance data correctly
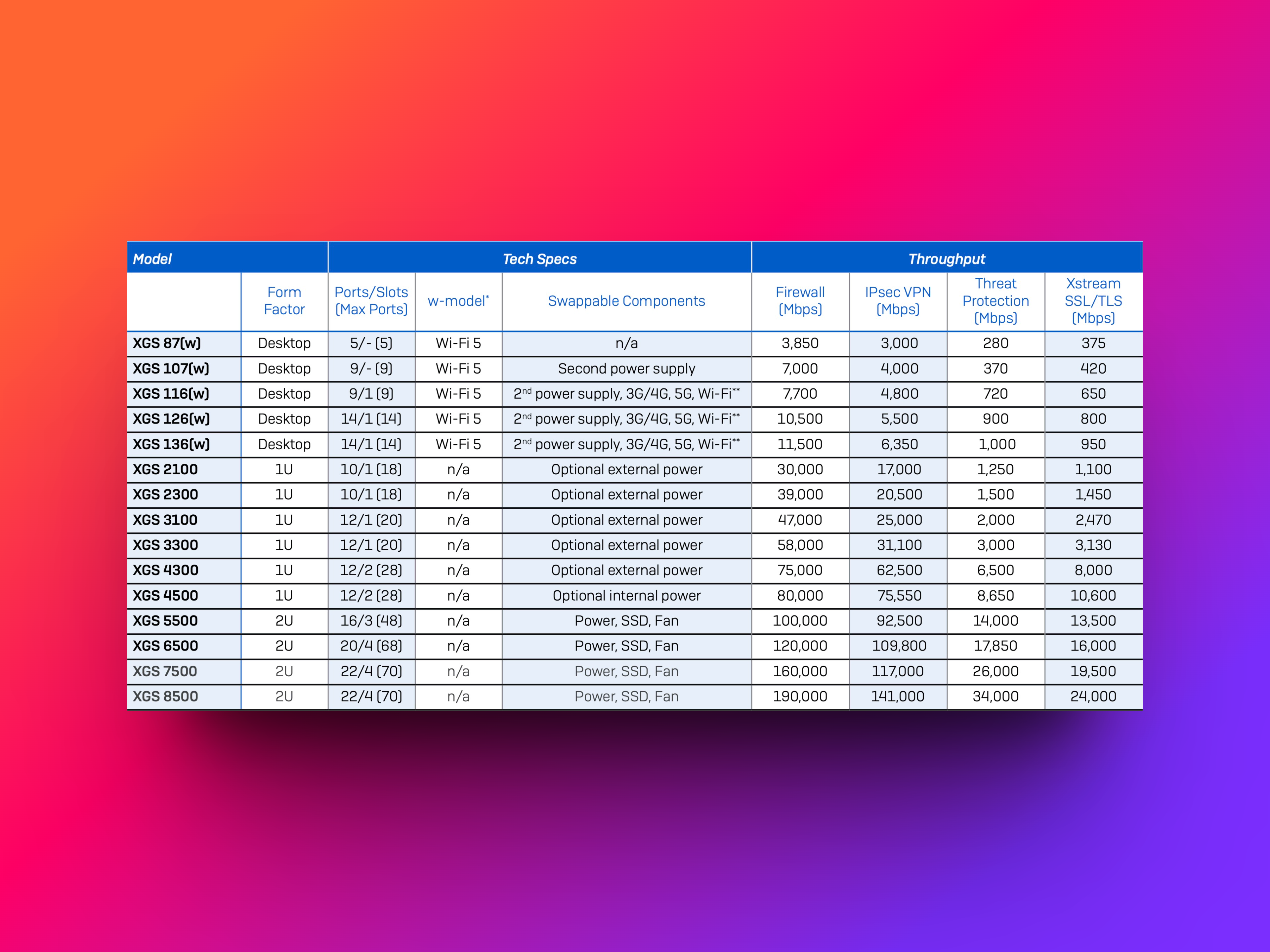
You can find firewall performance data on our product page, in the firewall comparison table, or in the Sophos firewall datasheet. To choose the right model, it is important to understand the Sophos Firewall performance data correctly.
Our Sophos Firewall Sizing Guide explains what to look for when choosing a firewall. To choose the right model, it is also important to understand the performance specifications of the Sophos Firewall.
The performance of your Sophos Firewall is a critical factor in the security and efficiency of your network. In this blog post, we will highlight the different aspects of Sophos Firewall performance analysis and explain how to interpret the performance data correctly.
Performance testing methodology
How is Sophos performance data generated?
Firewall performance is typically measured under ideal test conditions. Sophos uses the industry-leading Keysight-Ixia Breaking Point performance test tool for this purpose.
Keysight’s Ixia BreakingPoint is a recognized performance testing tool used to evaluate the security, reliability and performance of networks and network devices. It is often used to test the maximum capacity, performance and security of network devices such as firewalls, intrusion prevention systems (IPS) and routers.
BreakingPoint simulates realistic traffic as well as different types of threats, including malware, DDoS attacks and other security risks. It is able to generate a large amount of traffic to test how network devices react under high load and stress situations. It also enables how devices respond to various security risks and tests the effectiveness of security mechanisms.
For a firewall like Sophos Firewall, BreakingPoint can be used to determine how the firewall performs under various conditions. For example, it could be used to test how fast the firewall can process data (throughput), how it responds to certain types of threats (security testing), and how it behaves under heavy load (performance testing).
It is important to note that BreakingPoint test results are obtained under ideal test conditions and that actual performance in a real network environment may vary due to various factors.
However, it is important to note that the actual performance of your firewall can be affected by a variety of factors. These include the number of concurrent users connected, the type of traffic, and the security services enabled on your firewall. Therefore, to ensure optimal performance, it is important to regularly check the performance of your firewall and adjust it if necessary.
Firewall
Firewall performance is measured by the throughput of HTTP traffic. This throughput refers to the amount of data that the firewall can process in a given time and is usually expressed in megabits per second (Mbps) or gigabits per second (Gbps). The measurements are based on a response size of 512 KB.
To put this in a business context, imagine you have a file server in your company that many employees need to access. Every file access, download or upload of documents generates traffic that flows through your firewall.
Let’s assume that your firewall has a throughput of 1 Gbps. This means that it can process up to 1 gigabit of data per second. If an employee accesses a file on the Server that is 512 KB in size, your firewall can process this data packet very quickly because 512 KB is far below the maximum capacity of 1 Gbps. This ensures that the employee can access the required files quickly and efficiently without any significant delays.
Another scenario could be backing up your corporate data at night. When large amounts of data flow through your firewall, the firewall’s ability to handle high throughput becomes extremely important to ensure that the backup is performed efficiently and in a reasonable amount of time.
Firewall-IMIX
IMIX stands for “Internet Mix” and refers to a type of traffic that contains a mixture of different packet sizes. In the context of firewalls and networks, this is a useful concept for evaluating the performance of a system, as it provides a more realistic representation of typical Internet traffic than tests that use only one packet size.
When measuring the performance of Sophos Firewall with IMIX, the UDP throughput is measured using a combination of packet sizes of 66, 570 and 1518 bytes. This means that the firewall processes data packets of these three different sizes, which together represent rather realistic Internet traffic.
To illustrate this, imagine that your employees use different services over your network. Some send or receive emails (smaller data packets), others access files on the company server (medium data packets), and still others upload or download larger files or documents (larger data packets). These different actions generate data packets of varying sizes, all of which must be handled by your firewall.
By using an IMIX traffic profile, Sophos Firewall can simulate these mixed packet sizes to measure firewall performance under more realistic conditions. This type of measurement gives you a clearer picture of how well your firewall can handle the actual mixed traffic it must process in a real enterprise environment.
IPS (Intrusion Prevention System)
An intrusion prevention system (IPS) is an important component of network security designed to identify and block known threats. It monitors network traffic for anomalies or signatures that could indicate malicious activity and takes action to stop them before they can cause harm.
The performance of the IPS is measured by HTTP traffic using a standard IPS rule set and an object size of 512 KB. The rule set basically consists of a list of criteria against which the IPS checks the traffic. If the traffic meets these criteria, it is classified as potentially malicious and handled accordingly.
To put this in a business context: An employee opens an email that contains a malicious link. When the employee clicks the link, a data packet is sent to your Server that may contain malicious code. If it meets the ruleset criteria, it is classified as a threat and blocked before it can cause damage to your network.
Measuring IPS performance is therefore critical to understanding how well your firewall is able to detect and block threats in real time. Higher IPS performance means more traffic can be scanned in less time, resulting in higher network security.
IPsec-VPN
IPsec VPN performance is measured by HTTP throughput, using multiple tunnels and an HTTP response size of 512 KB. Higher throughput means that more data can be transferred in less time, resulting in a faster and more efficient VPN connection.
TLS Inspection
The TLS inspection feature on Sophos Firewall allows you to monitor and control encrypted traffic. It allows the firewall to look inside encrypted traffic to detect and block potentially malicious content that would otherwise be hidden by the encryption.
As an example, you might imagine an employee accessing an encrypted website. Although encryption typically prevents the content of the website from being viewed by outsiders, TLS inspection allows Sophos Firewall to inspect the content to ensure that there is no malware or other harmful content. If the firewall detects malicious content, it can block access to the website to protect the organization’s network.
TLS Inspection performance is determined by measuring performance with IPS on HTTPS sessions and different cipher suites.
Threat Protection
Threat protection on Sophos Firewall is a comprehensive security solution that combines various technologies and features to protect your network from a wide range of threats. It includes features such as the firewall itself, the intrusion prevention system (IPS), application control, and malware defense.
Imagine an employee attempting to download a file from a website that is classified as potentially dangerous. Sophos Firewall would first check access to the website (firewall function), then check the contents of the file for known malicious code (IPS and malware defense), and finally check the type of file and the application used to download it (application control). If a threat is detected in any of these steps, Sophos Firewall would block the download, protecting the company’s network.
Threat protection performance is measured by enabling firewall, IPS, application control and malware defense. The measurements are performed with an HTTP response size of 200 KB.
NGFW (Next-Generation Firewall)
A next-generation firewall (NGFW) on top of Sophos Firewall is more than a traditional firewall. It includes advanced features, such as intrusion prevention systems(IPS) and Application Control, to provide a higher level of network security. It provides deeper and more granular control of network traffic, enabling more effective threat prevention.
Example: An employee attempts to access a cloud application that is not approved for corporate use, such as a personal cloud storage service. The NGFW on Sophos Firewall would detect this access attempt (through application control), verify the content of the request (through the IPS), and then block access to the service. These additional features allow Sophos Firewall to go beyond simply monitoring ports and protocols, and instead provide a deeper understanding and control of network traffic.
The performance of the Next-Generation Firewall is measured by activating IPS and Application Control with HTTP traffic. A standard IPS rule set and an object size of 512 KB are used.