Sophos Central Endpoint Intercept X – The solution against ransomware
Let’s look the facts in the face. Anyone who goes online with a computer today is exposed to so many dangers in one fell swoop that the only way to protect yourself against them is with a mixture of common sense, good antivirus protection and, at best, a firewall with a web filter behind the network. Shutting down the computer in the evening without catching malware is becoming more and more of a challenge!
Ransomware has now been in the headlines since November 2015, and for a long time there was no technical protection, only tips and advice for IT managers. With Sophos Intercept X , Sophos has now launched a product that complements your existing endpoint security solution and can protect against ransomware, zero-day exploits and stealth attacks.
In this blog post, we will leave the classic viruses, worms and Trojans behind and focus on the really bad kind, namely the so-called ransomware (encryption Trojans). In addition, of course, we show how Sophos can protect against this malware and what products are needed to do so.
What exactly is ransomware?
Imagine that you are unsuspectingly opening the attachment of an email and suddenly a message appears on the screen that your data has just been encrypted and you will not get it back until you pay a “ransom” for it. However, payment is not made in a familiar form, such as PayPal, credit card or bank transfer, because the transactions should be as anonymous as possible and cannot be traced. As if you weren’t already stressed enough after this incident, you then also have to deal with Bitcoins. Pretty brazen, isn’t it?
Ransomware – When you suddenly have to pay a ransom for your data.
Today’s hacker has found an incredibly effective way to make a lot of money in a very short time. The hacker, or rather, the hacker organization, thereby receives sufficient financial resources, with which a part can be reinvested in the further spread of ransomware. The risk of you or even your company becoming a victim of this is therefore increasing. Think about what your company data would be worth to you.
In the following video, Sophos explains the issue in 90 seconds:
Ransomware does not disappear
Ransomware is currently the most effective attack, which means that it will not disappear anytime soon. Your own data is encrypted and if you want it back, you have to pay. Private individuals also have data, not just companies. So everyone is at risk. Companies simply bear the greater risk here, as more users access the same data. Thus, it is enough for a single employee to catch something and the group drive is encrypted and the company comes to a standstill. For hackers, ransomware is a success story because it’s a billion-dollar business! If you haven’t done anything about it yet, you should definitely do something.
How can you protect yourself against ransomware?
When the topic of “ransomware” first came to the public’s attention, there were many guidebooks that showed IT managers what could be done against these crypto-Trojans. Basically, it was advised to train employees, actively make them aware of these threats, and create regular backups of company data. There was no software solution that could have detected such a Trojan. Antivirus software vendors were overwhelmed with these novel and quite intelligent Trojans, and some vendors still are. Sophos had then for the first time in December 2015 with Sophos Sandstorm a solution to defend against advanced persistent threats (APTs) and zero-day malware. That was at least a start. If you want to protect yourself against ransomware, we can recommend the brand new product Sophos Intercept X which we believe should be installed on every endpoint.
Update: Meanwhile, there are new products Intercept X Advanced and Intercept X Advanced for servers.
Fighting ransomware with Sophos Intercept X
Sophos Intercept X is, in our view, simply a must-have to effectively protect against these new threats. Intercept X is based on technology from security vendor Surfright, which was acquired last year. The first product from this acquisition was Sophos Clean. With Intercept X, this technology has now been integrated into Sophos Central and enhanced with new features. Threat pattern detection relies on behavioral analytics, attack vectors and Big Data. This allows malware to be detected without relying on updates or signatures. Signatureless detection also has the advantage of protecting against unknown malware and attacks from zero-day exploits.
CryptoGuard – An anti-ransomware innovation
One component of Intercept X is CryptoGuard. This feature protects against ransomware and immediately detects when files are encrypted. If this happens, the encryption of files is blocked and already encrypted files are automatically restored so that no data loss occurs.
You can see how this looks in practice in this video:
Killer feature is the analysis
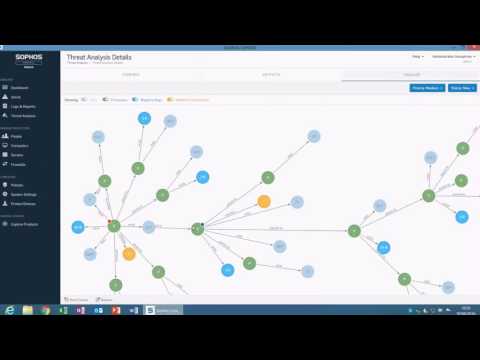
The icing on the cake comes at the end. Imagine that, despite all the protective measures, malware has made it into your network. How could this happen? Which devices have been infected and what should you do now? Intercept X’s “Root Cause Analysis Tool” can answer all of these questions down to the smallest detail. A 360-degree visual analysis helps you find out where the attack took place, which parts of the system were affected and where it could have been stopped. In addition, recommendations for action are provided for similar attacks in the future. You can see exactly what this looks like in the following video:
Additional protection to the existing antivirus
Choosing the right antivirus package is almost overwhelming. There are, for example, Symantec, McAfee, Kaspersky, Trend Micro, Avira and Avast, just to name a few. Chances are very high that you have one of these products in use. With Intercept X, you don’t have to change a thing! It is even desirable, because Sophos Intercept X can or better must be installed in addition to existing endpoint security solutions from any vendor, thus increasing the level of security.
Intercept is not an alternative to an antivirus, it is an additional layer of protection.
Sophos Intercept X can of course also be used together with Sophos Central Endpoint Standard (NEW!) or Advanced, providing a powerful additional layer of protection.
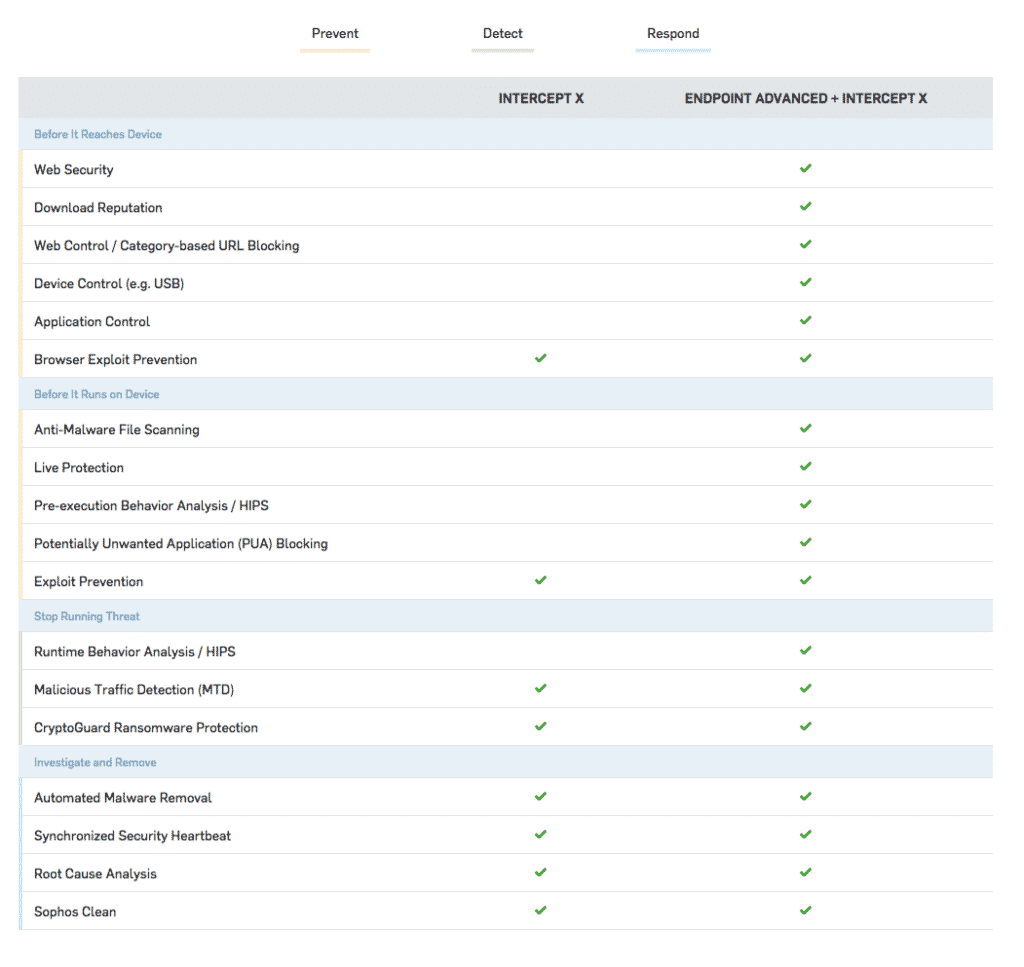
Intercept X management
Intercept X can be installed and managed via the cloud-based management console Sophos Central. Administrators can control and configure settings, issue licenses, add new endpoints and track all activity.
System requirements
Intercept X works smoothly alongside your existing antivirus software. Whether this is McAffee, Kaspersky, Symantec, Trend Micro, Avira, Avast or any other endpoint protection.
According to our contact at Sophos, a Mac solution is on the way and will also be built into Intercept X.
Try Sophos Intercept X now!
To see Sophos Intercept X for yourself, you can try it for free for 30 days. To do this, you simply need a Sophos Central account.
If you don’t have a Sophos Central account yet, you can create one on the Sophos website and try all the features, including “Sophos Intercept X”, for free for 30 days.
If you already have a Sophos Central account and the 30 days trial period has already expired, you can either order a license for “Sophos Intercept X” in our store or you can choose our “Sophos Central Subscription” and rent the licenses on a monthly basis according to the “Pay-As-You-Go” principle:
Ransomware Simulator
If you don’t quite trust this yet and feel that you are protected against ransomware even without Intercept X, check out KnowBe4 ‘s independent and free trial program “RanSim”. With this tool you can test whether your system could be infected by ransomware.