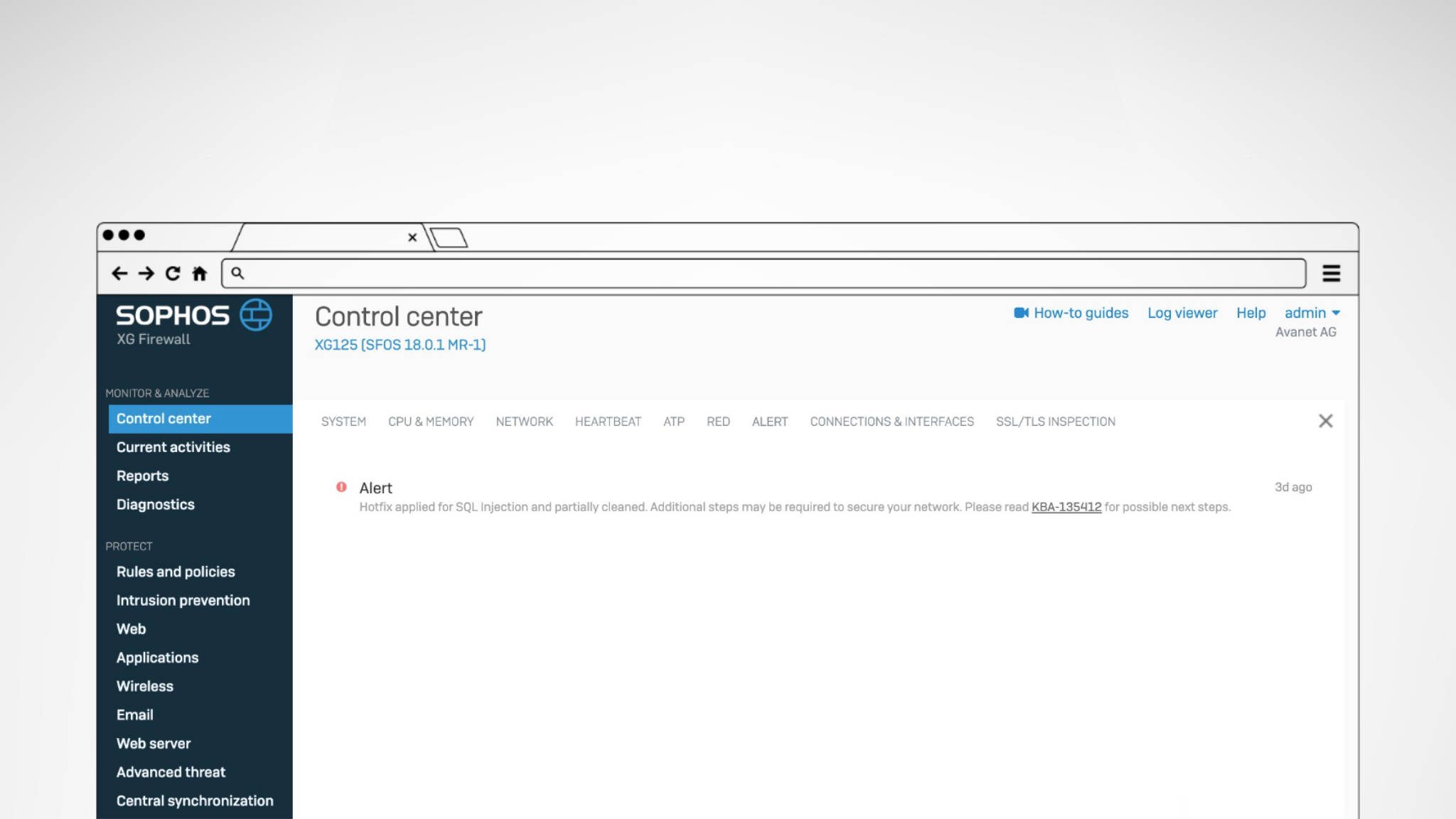
Sophos SFOS SQL injection vulnerability closed
There was a vulnerability in Sophos Firewall OS, which was also actively exploited. Sophos has already distributed the hotfix, but firewall administrators must change all local passwords.
What happened?
Admittedly, it is somewhat confusing for the normal user when a firewall that should protect the IT infrastructure is itself insecure. In fact, every device that runs software has security vulnerabilities. Often, these have simply not been found yet.
Sophos was notified of a zero-day vulnerability by a user at 20:29 on April 22, 2020. The attack had been going on for 5 hours at that point. The user noticed it because this was visible in the Admin Portal. The notification to Sophos regarding this vulnerability showed its effect at 10 p.m., when the first domains were blocked. In parallel, the cause was found and work on a solution was underway. On April 25, 2020 at 07:00, 63 hours after the first attacks, a hotfix could be distributed to all firewalls running SFOS.
This vulnerability made it possible for attackers to tap all local user names with the password hashes via the Internet. So in the worst case, someone could have gained access to the firewall. However, the password hash would have had to be reconstructed beforehand. This incident again shows that it is essential to use complex, long and strong passwords!
Who is affected?
All systems on which the Sophos Firewall OS (SFOS) has been installed. These can be SG appliances, XG firewalls or even VMs. These systems are compromised, but it does not mean that you have been hacked. The firewalls that were accessible from the Internet via the HTTPS Admin Service or the User Portal were at risk (see the screenshot below). If an admin has changed the default setting so that a firewall service such as SSL VPN listens on the same port as the two portals, this firewall will also be affected.
What needs to be done?
The Trojan named Asnarök exploited a previously unknown (zero-day) pre-auth SQL injection vulnerability. Sophos recommends changing all local passwords on the firewall. This means the admin password and all other passwords of users created on the firewall itself. Users that are loaded from e.g. an ActiveDirctory on the firewall are not affected.
- Change admin password (Superadmin password of the firewall)
- Restart firewall
- Change all other local passwords
For customers with a maintenance contract, we have already ensured that all necessary steps have been taken.
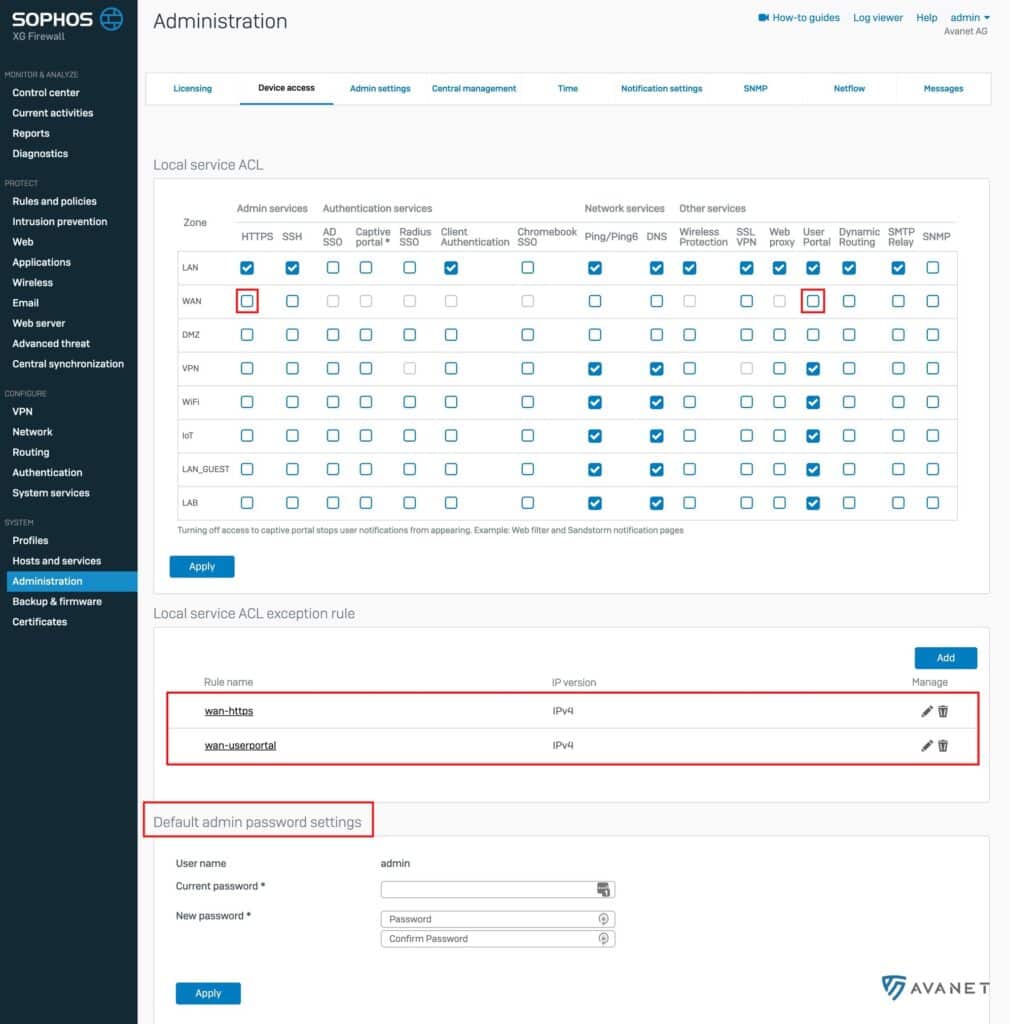
- On the screenshot you can see which checkboxes should not be activated. This opens access from the Internet to the firewall.
- Further down, you can define manual rules so that access to the firewall is only possible from one IP, for example, which already makes access much more secure.
- At the bottom, you can see where the admin password needs to be changed.
Hotfix
Sophos has rolled out the hotfix that closes the vulnerability via autoupdate. The feature that automatically installs updates is enabled by default.
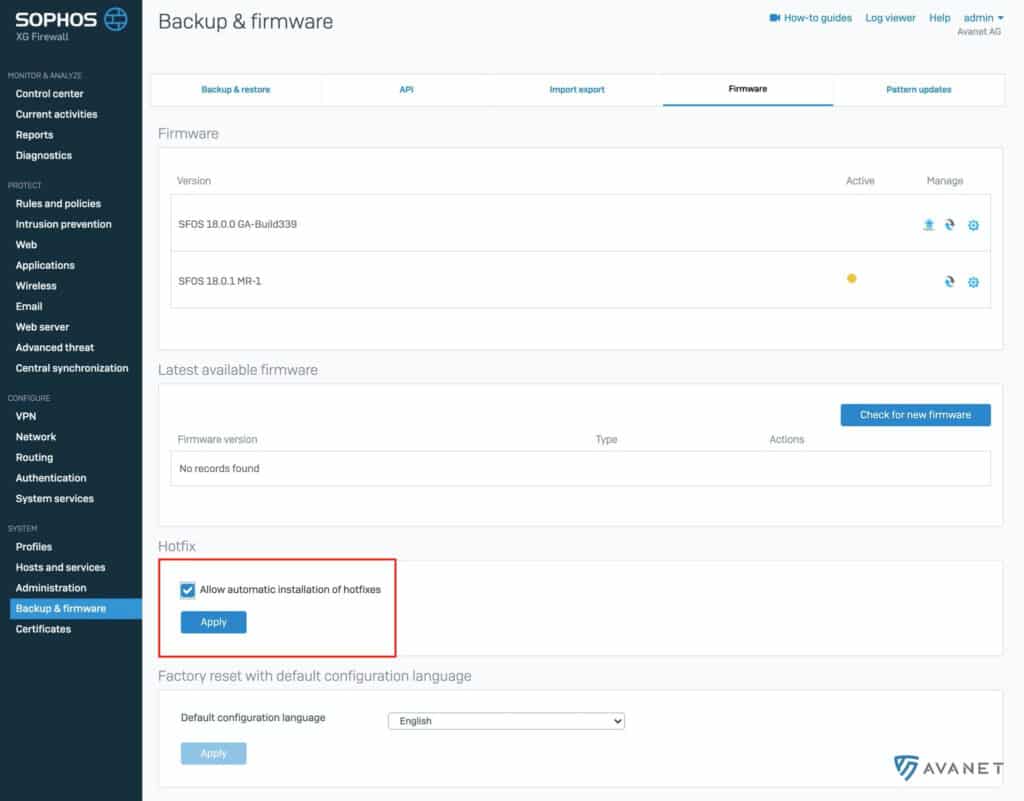
All firewalls with SFOS 17.x or higher have received the patch. If your firewall is still running version 15 or 16, this is also affected and must be updated.
More information
If you read our blog often, you know that we do nothing but deal with Sophos products all day long and earn our money with services and support. Although, as the saying goes, you should never bite the hand that feeds you, we try hard not to always see everything through rose-colored glasses. We always write what we think and that can of course also be critical words. So without sugarcoating anything now, as always, honest feedback:
In our view, Sophos provided information very quickly and transparently. Many other manufacturers often keep a very low profile and you never really find out what’s happening.
Sophos, on the other hand, informed the community within a short time with a KB and blog post, and we as Sophos partners also received an email on Sunday (even in 8 copies). Thus, the information was first published by the manufacturer itself and not by news sites, which is also not the norm.
In the Knowledge Base you get all the information about what exactly happened and how to proceed. Here in the blog are only the most important information, which should already be enough for many.


