
Sophos Firewall OS (SFOS) update v17.5 – MR3 released
Sophos has released version 17.5 MR3 for Sophos Firewall OS (SFOS). You can download the new firmware immediately from the MySophos portal .
In the next few days, the new firmware will also be available automatically via the firewall’s WebAdmin and can be installed with a simple click.*
Note: For more information on upgrading, see the following post: Sophos Firewall: How to upgrade the firmware .
*However, only those who have paid for Sophos Enhanced Support can benefit from this somewhat more convenient option. Sophos Enhanced Support is automatically included with every bundle (EnterpriseProtect, EnterpriseGuard, TotalProtect, FullGuard), but can also be purchased separately.
What happened to MR2?
SFOS 17.5 MR2 was released as a silent release, exclusively for NSS Labs. NSS Labs has once again put the XG Firewall through some tests before everyone can now enjoy the new features and bug fixes with MR3.
APX Support
When the new APX series of Sophos access points was released in July 2018, they could only be used with Sophos Central Wireless. Sophos already announced at that time that support for the XG Firewall would follow in December 2018. Today, with a delay of two months, the APX access points can now also be managed via the XG Firewall. 🎉
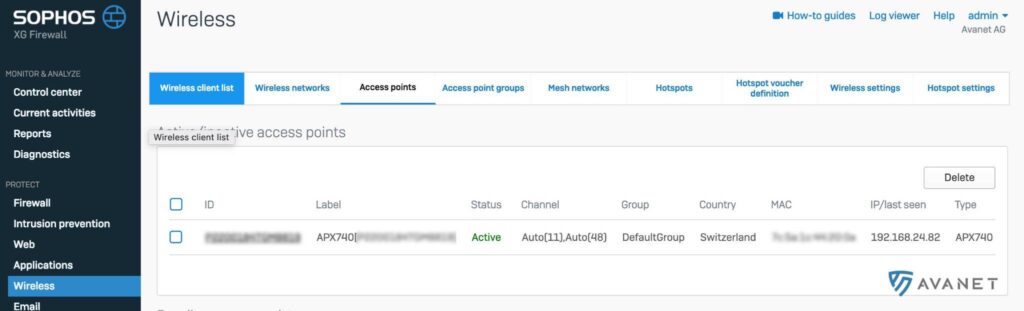
We immediately tested the XG Firewall Support with our APX 740. Since we previously operated this via Central, the link had to be removed first. After that, the access point was immediately displayed on the XG Firewall. The link worked without any problems. 😅
If you have an XG firewall in use and need new access points for it, we recommend only considering the APX series. For SG Firewalls with the UTM operating system, the normal AP models are still available.
- Sophos APX 120 (Sophos Central only! XG support has been scheduled for mid-2019)
- Sophos APX 320
- Sophos APX 530
- Sophos APX 740
Email Recipient verification using Active Directory
Since the engine of the UTM is now also running on the XG firewall, the last features are now also gradually being transferred to the XG. It is possible in SFOS v17.5.3 that a recipient verification can be made by means of Active Directory lookup. So it is checked in advance if the mailbox or email address exists on the mail server before the email is sent.
Airgap Support
Airgap is a feature that was already announced with SFOS 17.5. XG Firewalls can now also be licensed and updated offline with this function. The firmware could already be updated offline, but the pattern update is only possible with this firmware.
Bridge Interface – DHCP Client Support
Bridge interfaces can now receive IP4 and IP6 IP addresses and DNS information via DHCP.
Bug fixes
- NC-29354 [API] Response for xmlapi get for SyslogServer is missing some value
- NC-29808 [API] API Authentication should be case insensitive
- NC-35920 [API] Wrong XML is generated for client-less users when username added with capital letter
- NC-30616 [Authentication] Guest username/id and passwords are changed after migration
- NC-33449 [Authentication] Group name showing under “undefined” during AD group import
- NC-35923 [Authentication] XML export of guest users contains wrong information of user validity
- NC-38607 [Authentication] Provide a JSON config download for GSuite in the XG UI
- NC-39026 [Authentication] Chromebook Support port is missing in port validation opcode
- NC-39106 [Authentication] Access_server is restarted due to missing service heartbeat
- NC-30365 [Base System] Fix error message for new firmware check on auxiliary device
- NC-37824 [Base System] SFM/CFM – at device dashboard AV version shows as 0
- NC-38546 [Base System] Fix log message for scheduled backup and update message
- NC-39177 [Base System] Garner – sigsegv_dump: Segmentation Fault
- NC-39179 [Base System] Customization of captive portal not working
- NC-39688 [Base System] Virtual firewall reboots after applying license
- NC-40157 [Base System] Garner service stopped with sigsegv_dump: Segmentation Fault
- NC-40268 [Base System] Not able to access HA device via Central Management
- NC-38469 [Email] Increase csc monitor time for avd service
- NC-38521 [Email] Add support for recipient verification via AD using STARTTLS
- NC-39827 [Email] Improve documentation for mail spool and SMTP policies
- NC-35434 [Firewall] csc worker gets killed causing errors in port forwarding
- NC-35521 [Firewall] Import of exported config does not recreate the device access permissions correctly
- NC-38318 [Firewall] XML change and revert details are not generated for “firewall group” entity when create firewall rule from SFM device Level
- NC-39316 [Firewall] Group edit fail when user edit existing group and new name have double space
- NC-39605 [Firewall] Modifying one time schedules fails, if timer has already triggered
- NC-40080 [Firewall] Improve UI and help for group creation based on EAP feedback
- NC-29296 [IPsec] Charon does not reconnect in all cases
- NC-29365 [IPsec] IPSec tunnel fails when there are whitespaces at the begin or end of the PSK
- NC-30599 [IPsec] Checkboxes on IPSec UI pages do not work using Safari
- NC-38824 [IPsec] Spelling error in message when IPSec cannot be established
- NC-38946 [IPsec] Child SA going down randomly with Checkpoint IPSec connection
- NC-38603 [nSXLd] Custom URL web category list stopped working after updating to v17.1MR2
- NC-38958 [Reporting] Smart search filter is not working properly for “is not” filter in log viewer
- NC-39530 [Reporting] Logo is too close to the name of the report page
- NC-39770 [Reporting] ‘Context’ column getting removed after click on Reset to default for web content policy logs
- NC-39479 [Sandstorm] Dashboard message not correct for Single Scan Avira with Sandstorm
- NC-35750 [SecurityHeartbeat] Heartbeat widget not displayed on slave node when registered
- NC-38778 [SNMP] Unable to fetch the value for particular OID in SNMP server
- NC-35490 [Synchronized App Control] Application are not classified in Synchronized Application Control list
- NC-32342 [UI Framework] Restrict number of connection from particular IP at a particular time
- NC-39078 [UI Framework] Update Apache Commons Collections (CVE-2015-7501, CVE-2015-6420, CVE-2017-15708)
- NC-39081 [UI Framework] Update Apache Commons FileUpload (CVE-2016-3092, CVE-2016-1000031)
- NC-39910 [UI Framework] Policy Tester is not working via Central Management
- NC-38295 [WAF] WAF Rules not working after HA takeover
- NC-31388 [Web] URL Category Lookup doesn’t allow punycode-encoded domain names
- NC-31485 [Web] Skipping sandbox check is not being exported in the XML for WebFilterException
- NC-35585 [Web] Only 10 cloud applications are listed if the screen resolution is 2560*1440 or higher
- NC-36320 [Web] AppPolicy becomes DenyAll if all “characteristics” and any classification selected


