
Sophos XG Update v17.5 – All new features at a glance
We installed the second beta of the new SFOS 17.5 firmware at the beginning of November and took a closer look at it. At the Sophos roadshow in Dübendorf in March 2018 , there was still talk of a version 17.2 and 17.3, but Sophos has decided to pack up all the planned features and jump straight to version 17.5.
We can already anticipate one thing in this report: The SFOS 17.5 triggers rather mixed feelings in us. There are cool new features, but from our point of view they were not always thought through to the end.
Lateral Movement Protection
Since the first version of Synchronized Security, it is possible for the endpoint client to share its state with the firewall. Thanks to this feature, we can, for example, deny access to the file server or the Internet to a workstation that has not received any updates for a while, or is already infected, so as not to endanger other systems.
Until now, however, such a configuration also required good network segmentation. If all devices in a company are connected to the same switch and they are on the same network, the security heartbeat hasn’t really had an effect so far.
With SFOS 17.5, this feature has been expanded and improved. It is now also possible to isolate computers classified as “unhealthy” by Synchronized Security from other computers in the same broadcast domain or network. The firewall automatically informs all other clients if there is a problem with one client. So now not only the firewall knows if something is wrong with a client, but also all other clients in the network. This allows an infected device to be isolated even more effectively until the problem is fixed. As soon as the security heartbeat status changes back to “green”, the connection to other systems in the network is automatically restored.
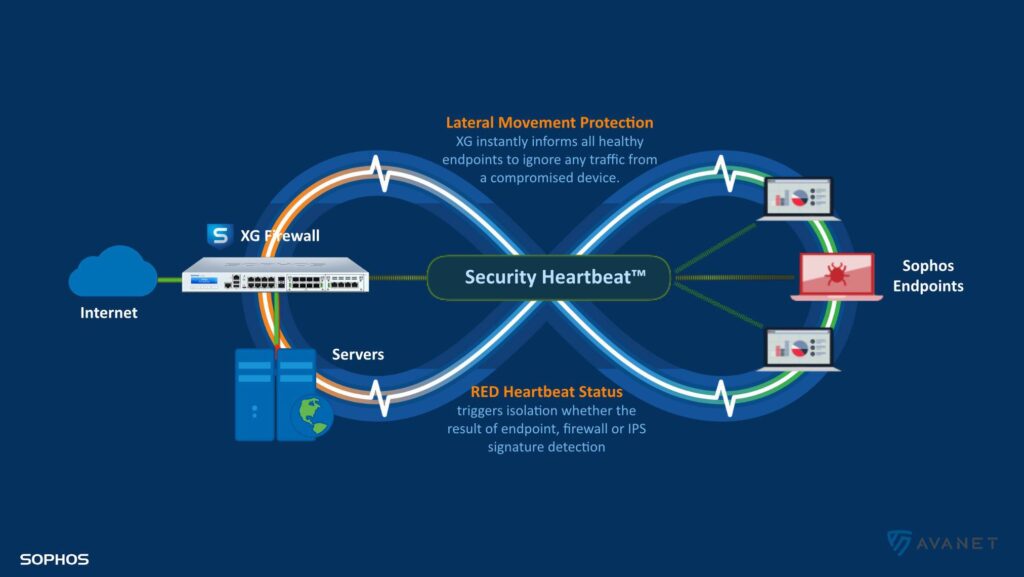
Additionally, IPS detections of vulnerable endpoints can now trigger a “red” heartbeat. This further improves protection against threats on the network.
Forwarding from portal URL
During my tests, I noticed a feature that has been sneaked into the new version, because it is not mentioned anywhere in the release notes.
I’m sure you’re all familiar with this. When a website is blocked by the Sophos web proxy, a warning page is displayed to the user. If the user wants to visit the page anyway, the link used to hide an IP address instead of a normal URL. In version 17.1 it was possible to change this via the console. With 17.5, this can now also be done conveniently via the web interface of the XG Firewall. 👍
Switching from an IP address to a web URL only works for the web part! For example, when XG Firewall scans your emails, it is common for users to receive a quarantine report from the firewall. This then shows which emails the Sophos Firewall has blocked. By clicking on a link, you can manually release the supposed spam message. However, this very link is still an IP address, which technically works, but issues a certificate warning for the user.
Switching from an IP address to a web URL was not finished for the email part. I have received feedback from Sophos that it will be followed up with MR1 or MR2 at best, and that the developers are working on it. My guess would be MR2, which means we can expect it around January or February.
Synchronized User ID
One of the most common tasks that a firewall has to perform is to transport traffic from A to B, provided that a firewall rule has been created for this purpose. Traffic comes and goes to one IP address at a time. We as administrators would like to know from which devices the traffic is generated or even better from which user. This helps us to create user-based firewall rules, create network transparency or generate more understandable reports.
On the SFOS there are a few ways to recognize the user. In the past, we used to connect to an Active Directory server for this purpose, which forwarded the user information through an installed agent of XG Firewall. In some environments, however, the agent was not an option.
With SFOS v17.5, endpoints on an Active Directory domain can now share user identity with the firewall via the security heartbeat. This makes user identification seamless and easy without the need to deploy an agent on domain controllers. This function can be very helpful in many situations.
Terminal servers or Linux hosts are not covered by this solution. For the former, STAC is still the best solution. However, the exceptions are great. Mac clients do not work with an Active Directory and VPN users do not log in to it either.
You can only benefit from this feature if one of these products is installed on the clients:
In my opinion, it becomes interesting when clients that are not in a domain also share their user data with the XG. This function solves only a very small problem.
Sophos Connect IPSec VPN Client
Our post Install SSL VPN Client is one of the most popular posts in our Knowledge Base. This is not without reason, because for many of our customers VPN was one of the most frequently mentioned requirements before purchasing the Sophos Firewall.
As described in this guide, we currently use the SSL VPN client from Sophos very often. However, this can only be installed on Windows computers. For macOS, you previously had to resort to third-party tools, such as “Tunnelblick”.
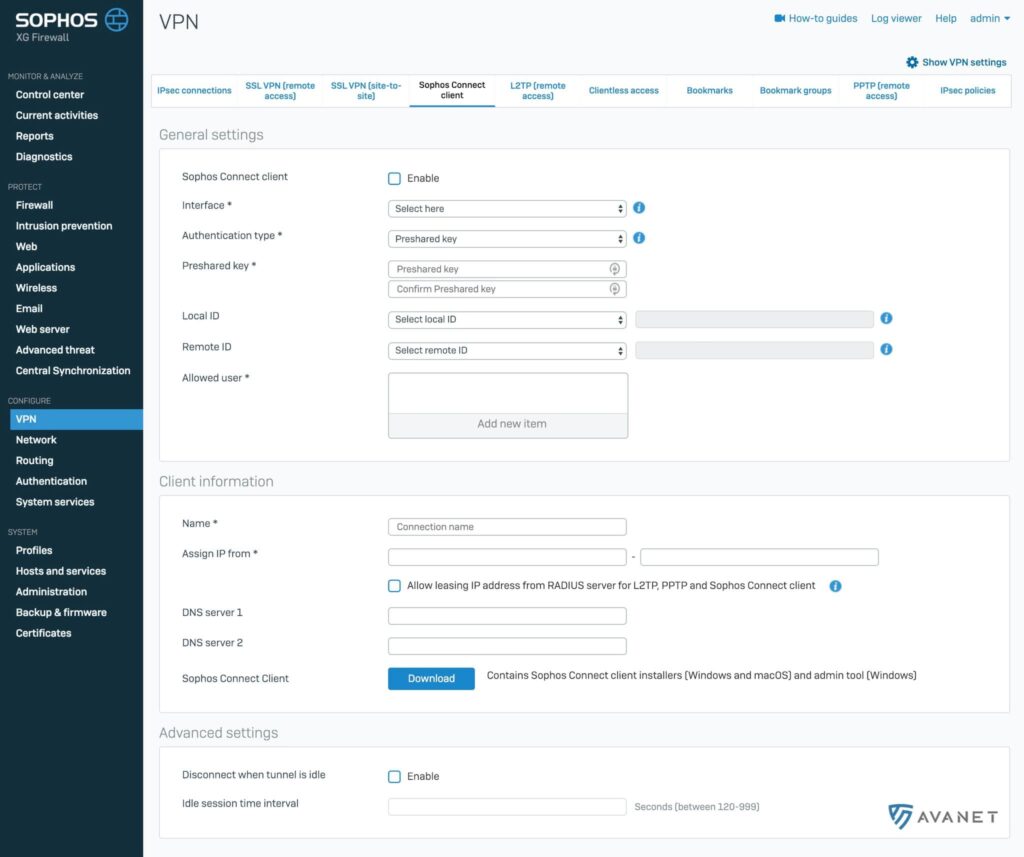
With Sophos Connect, Sophos is now introducing its own IPsec VPN client, as other manufacturers are doing. Sophos Connect also natively supports Synchronized Security. Until now, this also worked with the SSL VPN client, but it had to be configured additionally.
Here is a screenshot of how the Sophos Connect IPsec VPN client settings look on the XG Firewall:
Sophos Connect is currently in beta and the client is currently available for Windows and macOS. Here is another screenshot of the Mac and Windows client:
The new IPsec VPN client from Sophos is accompanied by “Sophos Connect Admin” as an additional tool. This allows you to edit a config file afterwards and, for example, adjust the hostname or enable 2FA.
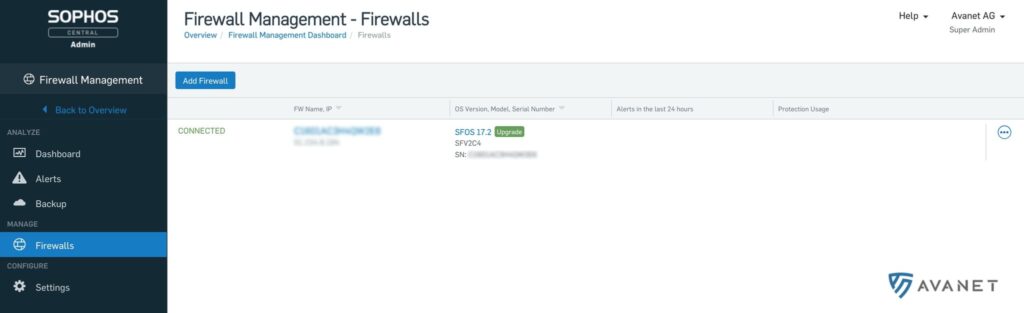
Sophos Central Management
With the new SFOS 17.5 firmware, a promise made a long time ago has finally been kept. The XG Firewall can now also be managed via the Sophos Central platform. Certainly the right step, but the functions are still limited in the first version.
To connect your Central Account to the firewall, you must first enable Central Management on the XG Firewall.
Update 20.11.2018 Sophos Central has since received an update, whereby the menu item “Firewall Management” is now visible. By enabling the Central Management feature on our XG Firewall, we were able to successfully add the device to our Sophos Central account.
When you connect to the firewall via Sophos Central, you are subsequently logged on to the firewall as “admin”. The unfortunate thing is that now, theoretically, other users who have access to Sophos Central Admin can get onto the firewalls. It is enough if these users have a ‘Read-Only’ permission. We hope that in the future it will be possible to control more precisely who exactly has the authorization to log on to the firewalls via Central.
Firewall management via SSO
If you have enabled the Central Management feature on your firewall, you can log in to the Sophos XG Firewall directly from the Central interface without any additional login.
Central Backups
By default, Central Management also stores the backups of your firewall on Central. If you don’t want this, you can simply disable this feature on your XG Firewall.
Central notifications
If the firewall is linked to Central, you will also see the firewall messages in the Central dashboard. This includes, for example, interface or VPN faults, as well as resource utilization, license notifications and security alerts.
Firmware update
In the future, it will be possible to update the firewall firmware from Sophos Central with just one click.
Light-Touch Deployment (Zero-Touch Deployment Option)
The “Light-Touch Deployment” is a really cool thing! In the future, it will be possible to configure a new XG firewall directly via Central. First you click through a small wizard, which spits out an XG config file at the end. This configuration can then be downloaded and copied to a USB stick. After that, the new firewall must be started with this stick and the configuration is transferred in the process. Once you have done everything correctly, you can access the firewall via Sophos Central and carry out the remaining configurations.
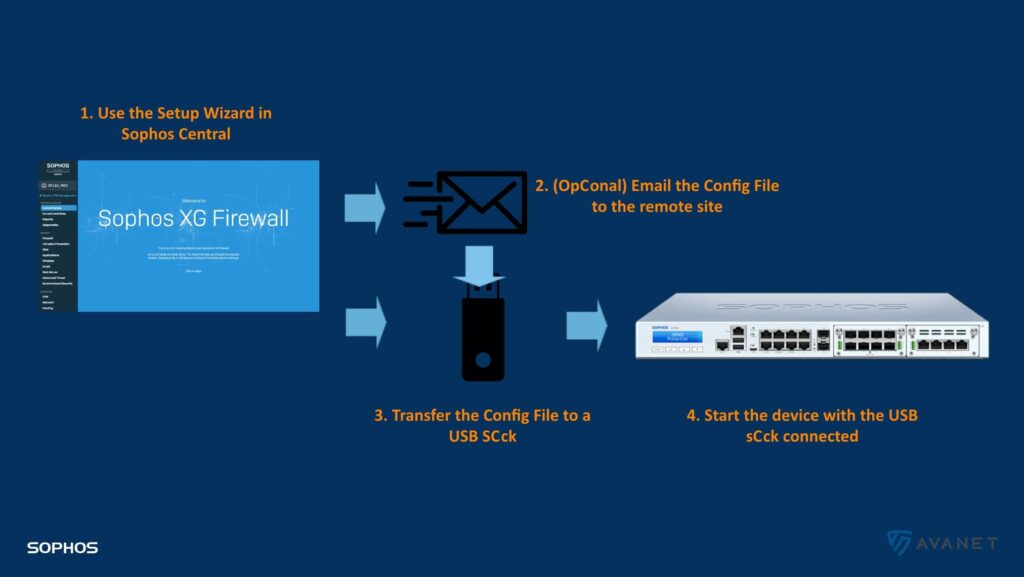
The “light-touch deployment” will make it much easier for us to set up XG Firewalls for our customers in the future. For our setup and configuration service we have the firewalls delivered to our office and create the basic configuration directly on the devices. We then send this to the customer, who only has to connect the firewall to the network. With “light-touch deployment,” we can save ourselves the trouble of having the hardware shipped to us in the future, which means we’re at least a day faster. 😎
Since this workflow requires a central account, we will probably not be able to use this procedure for every new customer.
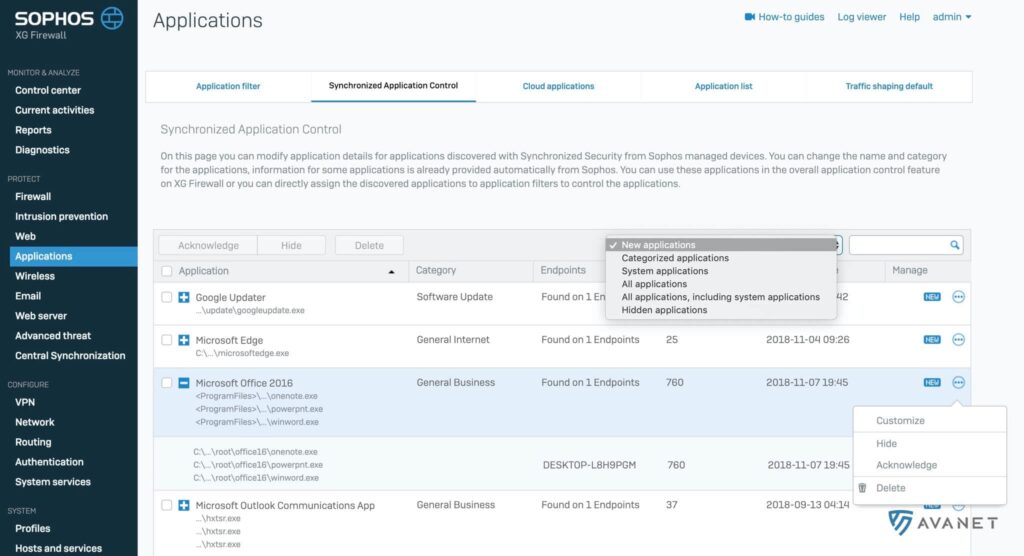
Synchronized Security – Synchronized Application Control Enhancements
Synchronized Application Control was first introduced with version 17.0 and further improved in version 17.1. With this feature, Sophos wanted to provide a solution to the basic problem that much of the network traffic is still difficult to control and can get through the firewall relatively undetected even with HTTP/HTTPS scanning. With Synchronized Application Control, the endpoint tells the firewall exactly which software is causing the traffic. Thus, network traffic can be classified much better.
With v17.5 the following improvements have been implemented:
- View Windows and Mac system applications in a separate list
- Hide apps and then use a new filter option to show hidden apps and show/hide apps.
- There is also a new option to mark applications to remove them from the “new” list.
- Improved display of path names
Log Viewer
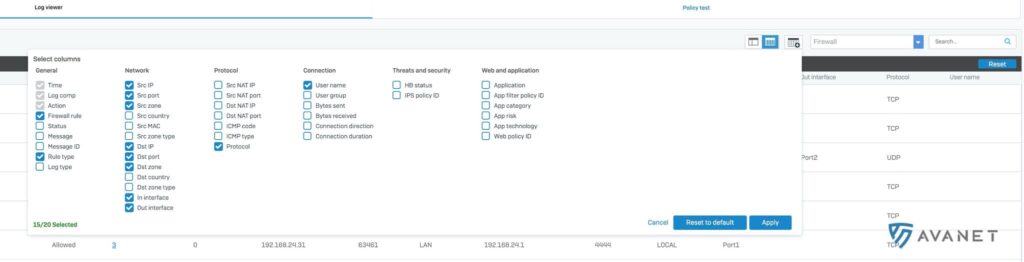
The log viewer is one of the things I’ve come to really appreciate about the XG. Every now and then he’s not the fastest, but I’m sure they’re working on that. With version 17.5 there is now the possibility to customize the view (user defined column selection). You can now choose for yourself which columns you really need.
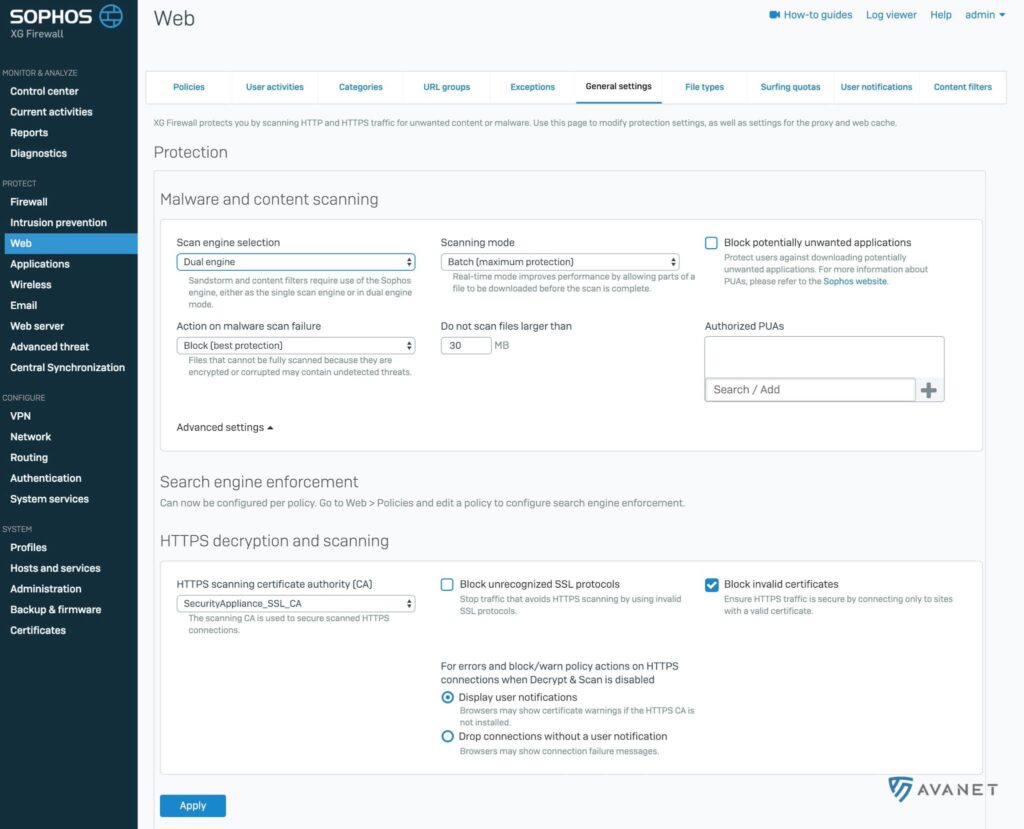
Web Policy Improvements
Imagine a teacher is working with his class on the computer and a needed website is blocked. In such a situation, the admin always had to be called to unlock the page. In SFOS version 17.5, there is now a feature in the web policies that allows you to allow authorized users to visit blocked web pages anyway. So you could give this teacher the possibility to simply unlock this website, domain or category yourself via the User Portal.
Each rule is given a code, which it can then communicate to the class. On the blocked page, students can then enter this code and temporarily get to the actual blocked website.
We as administrators can then see in a list which codes have been generated and can also delete them. However, the admin can also define locations or categories which cannot be bypassed by teachers.
Here are a few more small new features that will be available to you in SFOS version 17.5 in the web policies:
- Setting a default search engine
- SafeSearch and YouTube restrictions
- File size limitation during download
- Google App domain restrictions are all set on a policy-specific basis
Chromebook Authentication
Chromebooks are becoming more popular in education and some corporate environments (since Apple devices are getting more expensive) 😉. User identification for this operating system is different from other systems and was not supported by XG Firewall until now. With v17.5, Sophos offers a Chromebook extension that shares Chromebook user IDs with the firewall. This enables policy enforcement and user reporting. However, an Active Directory server is required, which synchronizes with Google Gsuite. The Chrome extension is launched from the Gsuite management console and offers easy deployment that is transparent to the user.
Client Authentication Agent
The XG Firewall Client Authentication Agent provides the possibility to tell the XG Firewall which user is currently logged on to the computer without using Active Directory. To do this, simply run the Client Authentication Agent on the device.
The client is available for Windows, macOS, Linux 32/64 bit, iOS and Android. You can find the download in the User Portal.
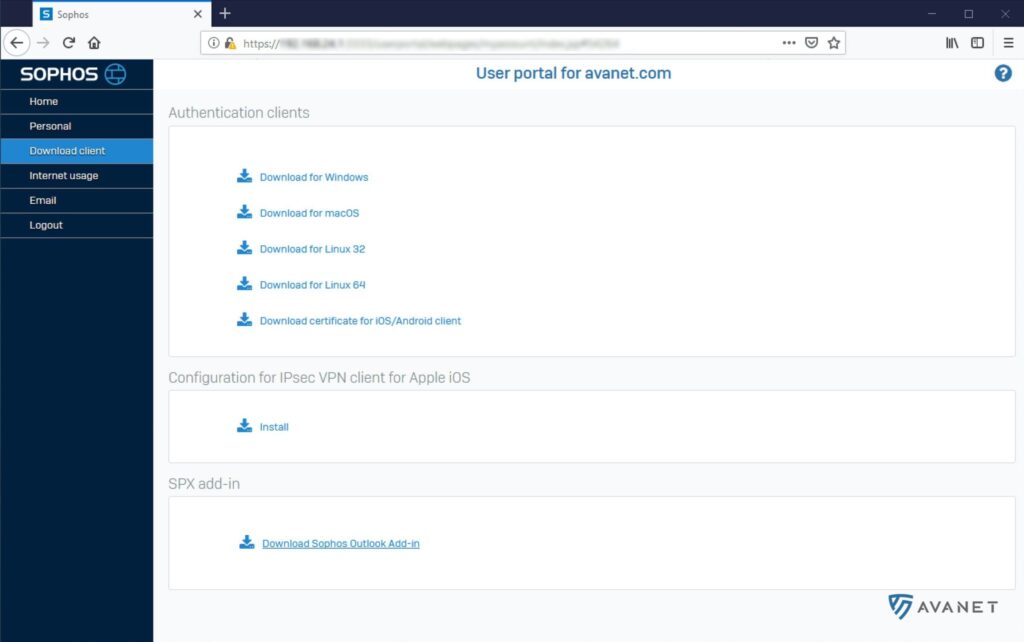
New there is now support for
- the installation per machine (and not per user)
- an option to hide at startup
- an option for the user to explicitly log off
- automatic reconnection when waking up from sleep mode
- MAC address telemetry sharing to support MAC address filtering
- a new taskbar icon
- Windows XP (for whatever reason this was still done)
Management improvements
When you create a new firewall rule, you can assign it directly to a group. There is also a new automatic group assignment, although this did not really work well for me. In my tests, the firewall wanted to automatically assign my rule to a group, but I didn’t want it in that group.
More improvements
- With 17.5, we switch back to the Exim engine, which is also used on the UTM.
- Recipient verification via Active Directory
- The Web Protection of SFOS is now almost identical to that of the UTM operating system.
- Sender Policy Framework (SPF) spoofing protection.
IPS Protection
- More categories to optimize the rules even better. Provides better performance and more protection.
Wireless
- Support for Radius server failover with multiple servers.
IPsec
- SD-WAN failover and failback
- IPsec Failover – Redundant groups for IPsec connections to switch to another WAN link in case of failover. As soon as the main connection is available again, it is also possible to switch back.
What’s coming in the next versions?
In the coming weeks / months maintenance releases will be released as usual, which will add some more features.
Sophos Wireless APX Access Point Support
Sophos’s new APX access points could sometimes only be used with Sophos Central. However, support for the XG Firewall is expected in MR1, which will be released about 2-4 weeks after the 17.5 release. The APX 120, which will then be available for purchase for under CHF 200, will not arrive until January 2019.
Airgap Support
There are XG firewalls that are not connected to the Internet. Unfortunately, license activation was not possible for these devices until now. There is a new option to download the license and updates to the firewall using a USB stick.


