Configure Sophos Connect Client on the Sophos Firewall (SFOS)
In this guide, we will show you how to set up the Sophos Connect Client for your employees as an Sophos Firewall administrator. SFOS 17.5 or newer is required.
Sophos Connect Client – Series
This article is part of a series that will give you everything you need to get started with the Sophos Connect client.
- Comparison: Sophos Connect Client or SSL VPN Client?
- Configure Sophos Connect Client on XG Firewall (SFOS)
- Install Sophos Connect Client on Windows
- Install Sophos Connect Client on macOS
Preparation
Log in to your XG Firewall as an administrator and go to VPN > Sophos Connect Client from the menu. On this page we will now go through the settings in 12 steps and make the necessary entries.
Please also note the following diagram with the steps marked so that you can follow the instructions more easily:
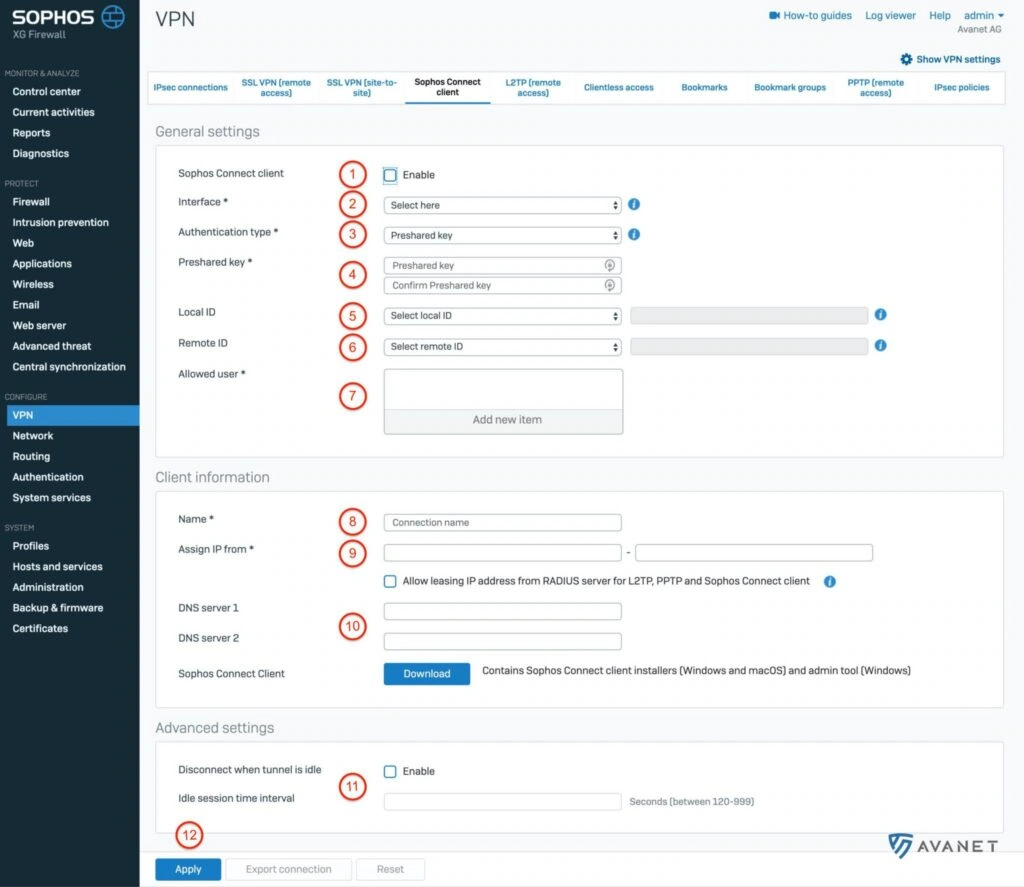
General settings
1. activate Connect Client
The beginning is quite easy. Check the box to enable the Sophos Connect client.
2. select interface
In this step, you need to select the interface on which the traffic will arrive on the Sophos. Typically, this is a WAN interface with a public IP address. If you have multiple WAN interfaces because you have more than one Internet provider, choose either the faster one, the more reliable one, or the one with less traffic. Decide for yourself which criterion is most important to you.
3. authentication type
You can choose two options here:
- Distributed key – Define a password yourself.
- Digital certificate – select a certificate in this option.
4. define distributed key
For this tutorial, we have chosen the Distributed Key method, which must now be defined at this point. If you have selected the Digital Certificate method, you can then select a certificate from your appliance at this point.
5. local ID (optional)
If you have multiple tunnels, you can define a local identification here so that the correct tunnel can be identified. There are the following options here:
- DNS
- IP address
- Certificate (if you have chosen the certificate at point 3)
6. remote ID (optional)
Here you can make the same selection as in point 5.
7. authorized users
If you already have users on your XG, or if you have synchronized the entire Active Directory, you can select the users/groups that are allowed to use the Sophos Connect client here.
Client data
8. name
Define a name for this IPsec connection here. In our example we have called the connection homeoffice.
9. assign IP from
The firewall assigns an IP address via DHCP to all users who connect through the Sophos Connect client. In this step you can define the IP range to be assigned. Select an area here that is not yet used on the firewall.
10. DNS-Server
It is often the case that VPN users want to connect to internal Server. For this purpose, it makes sense to work with the FQDNs as in the corporate network. Enter your internal DNSServer here.
If you do not have an internal DNSServer or do not need this function, you can also specify an external DNSServer, for example:
- Cloudflare: 1.1.1.1 and 1.0.0.1
- Google: 8.8.8.8 and 8.8.4.4
- Quad9: 9.9.9.9 and 149.112.112.112
- OpenDNS: 208.67.222.222 and 208.67.220.220
Advanced settings
11. session timeout
Experience shows that users do not always consistently disconnect a VPN connection when it is no longer needed. You can decide for yourself how you want to handle open connections here. The Sophos Connect client gives you the option to automatically disable the connection when no traffic has passed through after a certain time. In our example, we have configured the following:
- Abort connection when tunnel is inactive: enabled
- Time limit for inactive session: 120 seconds
This means that the connection is automatically closed by Sophos Firewall if no more data traffic has been registered by the client for 2 minutes.
12. save
To save your settings now, all you have to do is click on Übernehmen.
Set up firewall rule
In order for the firewall to now also allow traffic from VPN users, a firewall rule must still be set up for this. To do this, use the menu to go to Firewall and click on Firewall-Regel hinzufügen > Benutzer-/Netzwerkregel . Take a look at the following screenshot and try to set the rules exactly the same way.
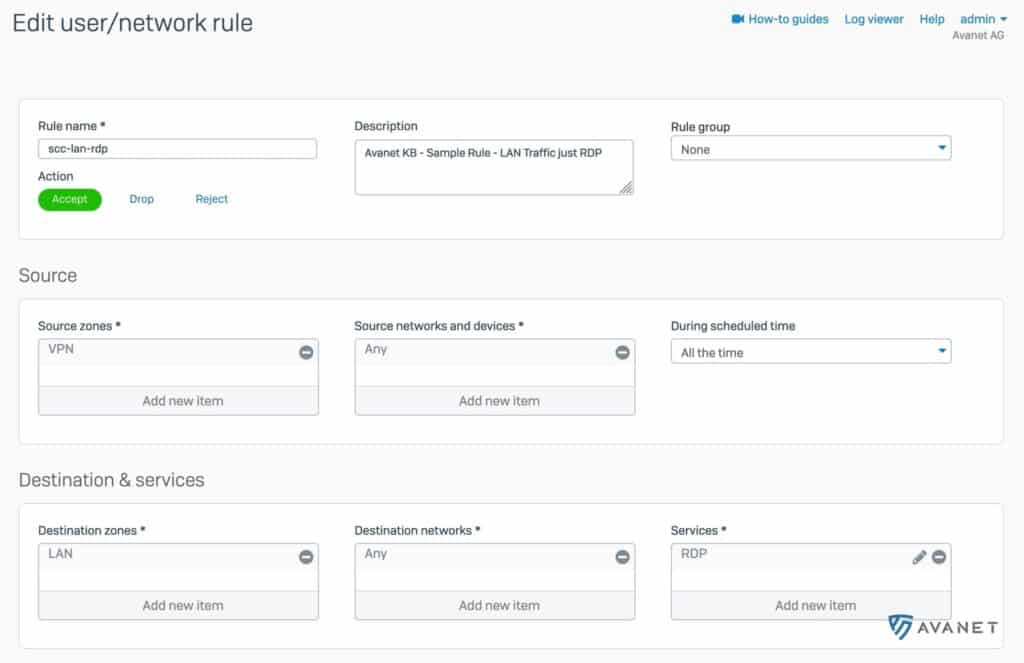
- Source Zone: VPN
- Destination Zone: LAN
By default, the Sophos Connect client routes all traffic through the IPsec tunnel. This means that Internet traffic is also sent through the tunnel. We have to allow this on the firewall first and create another rule for this.
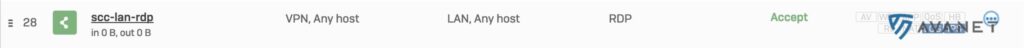
- Source Zone: VPN
- Destination Zone: WAN
Further information
After using this guide to configure the Sophos Connect client on your XG Firewall, you may want to go ahead and download and install the Connect client for Windows or macOS next.