Create Sophos ZTNA Gateway
This guide explains how to run the ZTNA Gateway on a hypervisor.
The different deployment modes of Sophos ZTNA
Sophos offers two different deployment modes for Zero Trust Network Access (ZTNA): the On-premise Gateway and the Sophos Cloud Gateway. Both modes have their own advantages and disadvantages and can be selected depending on the company’s requirements.
On-Premise Gateway
When using an on-premise gateway, the gateways are installed in the company’s own data center or on a hypervisor provided by the company itself. This means that you have to manage the gateways that are connected to the public Internet yourself. It is therefore necessary to open firewall ports and create NAT rules to manage the network. This mode offers direct control over the infrastructure, but also requires more administrative effort. However, the data connection is more direct, faster and without restrictions.
Sophos Cloud Gateway
In contrast, the Sophos Cloud Gateway enables access to internal resources via a Sophos-protected data plane cloud. This mode isolates network deployments from direct Internet exposure and reduces the attack surface. A major advantage of this deployment method is the ability to easily connect users to applications without having to open firewall ports and create NAT rules. Sophos is responsible for managing the data plans within the Sophos Cloud, which keeps the company’s infrastructure hidden from the Internet. The nearest access point can also be selected to minimize latency times, and availability is guaranteed at 99.999%.
Limitation: There is a traffic limit of 15 GB per user and month for the Cloud Gateway. With 10 users, this adds up to 150 GB for all users. This can quickly become scarce for companies that want to use ZTNA for network drives.
The two modes are interchangeable and companies can easily switch from one gateway mode to the other depending on what best suits their current needs. This offers a flexible solution that can adapt to the changing needs of a company.
Requirements
To configure the ZTNA gateway, you need the following things.
- Hypervisor, Cloud or Sophos Firewall
- Access to Public DNS
- Wildcard certificate
- Fixed IP address
- Access to firewall to create DNAT rule
Platform Support
The following platforms are supported:
- VMware ESXi
- Microsoft Hyper-V 2016 or higher
- Amazon Cloud AWS
- Sophos Firewall (ZTNA Cloud Gateway)
We recommend assigning 2 cores and 4 GB RAM to the VM. This is sufficient for 10’000 clients. If this is not enough for a company, it is also possible to cluster several gateways to increase the number to 90’000 clients by a cluster of 9 gateways.
Subnet for gateway
The ZTNA gateway should be operated in its own subnet and not used in the client or server network.
Do not use any of these networks for the gateway:
- 10.42.0.0/16
- 10.43.0.0/16
- 10.108.0.0/16
A DNS name e.g. ztna.domain.com points to the public IP address, which is forwarded to the ZTNA gateway via port forwarding (port 443).
On the one hand, the ZTNA gateway requires access to the Internet and to the respective VLANs of the applications that are provided, with the corresponding ports.
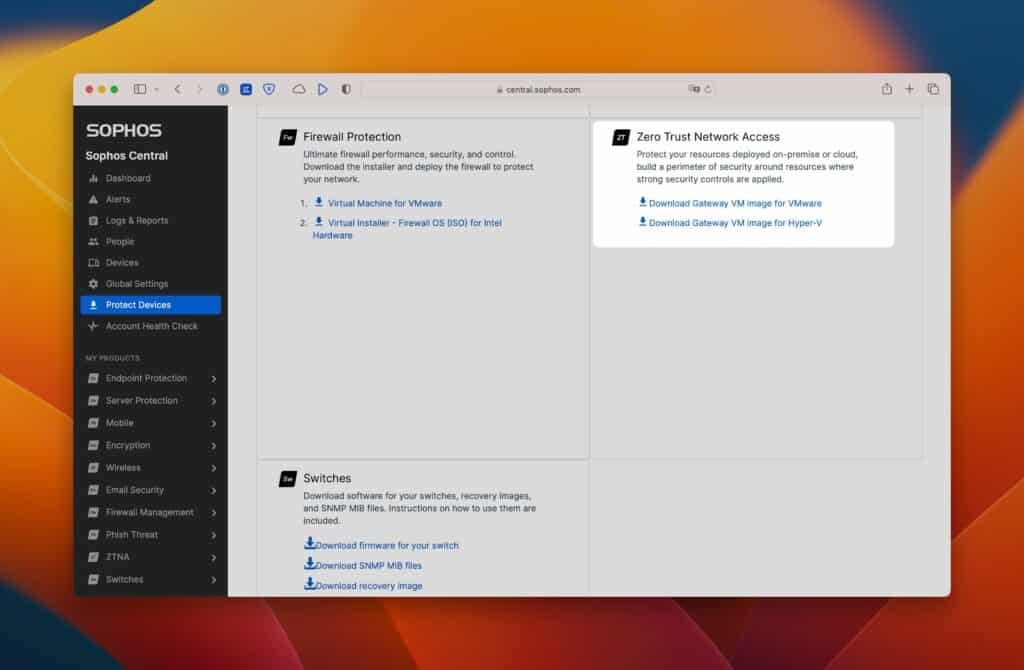
ZTNA Gateway Download
On Sophos Central in the main menu under Protect Devices, you can download the files for the virtual machine.
Deploy the VM on Hyper-V or ESXi
Create a new virtual machine with the following settings:
Generation 1 (for Hyper-V)
Virtual processors: 2
RAM: 4 GB
Network: Preferably own VLAN
Hard disk for Hyper-V: .vhdx files, which were previously downloaded.
ESXi: Uses the OVA file.
Before you start the VM, you have to create the ISO with the settings.
Gateway settings
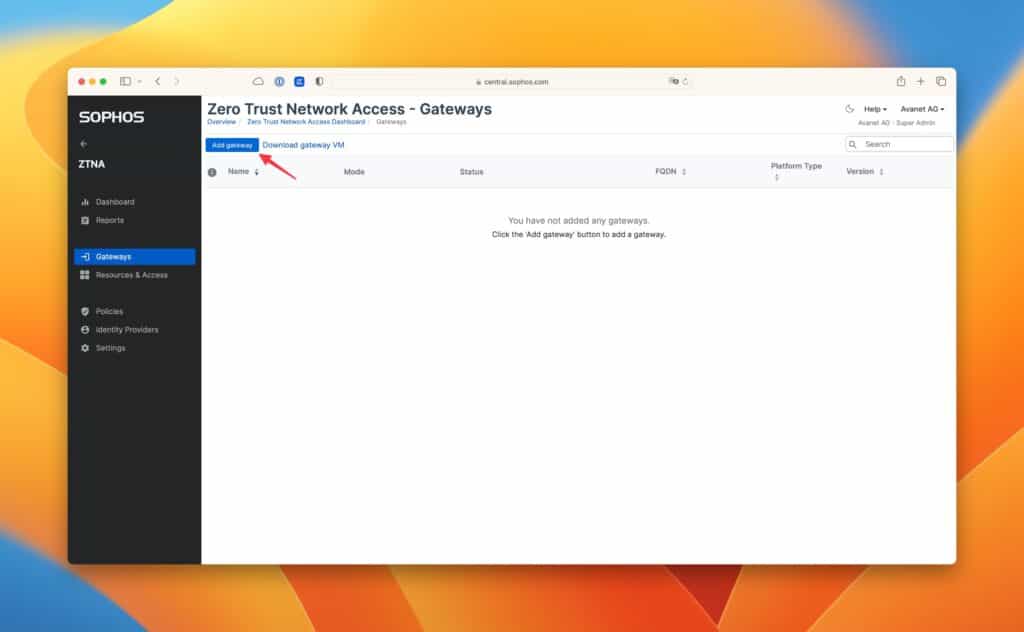
The VM has now been created, but it still has no settings and no reference to the Central Account.
These are now given by adding a gateway and making the settings.
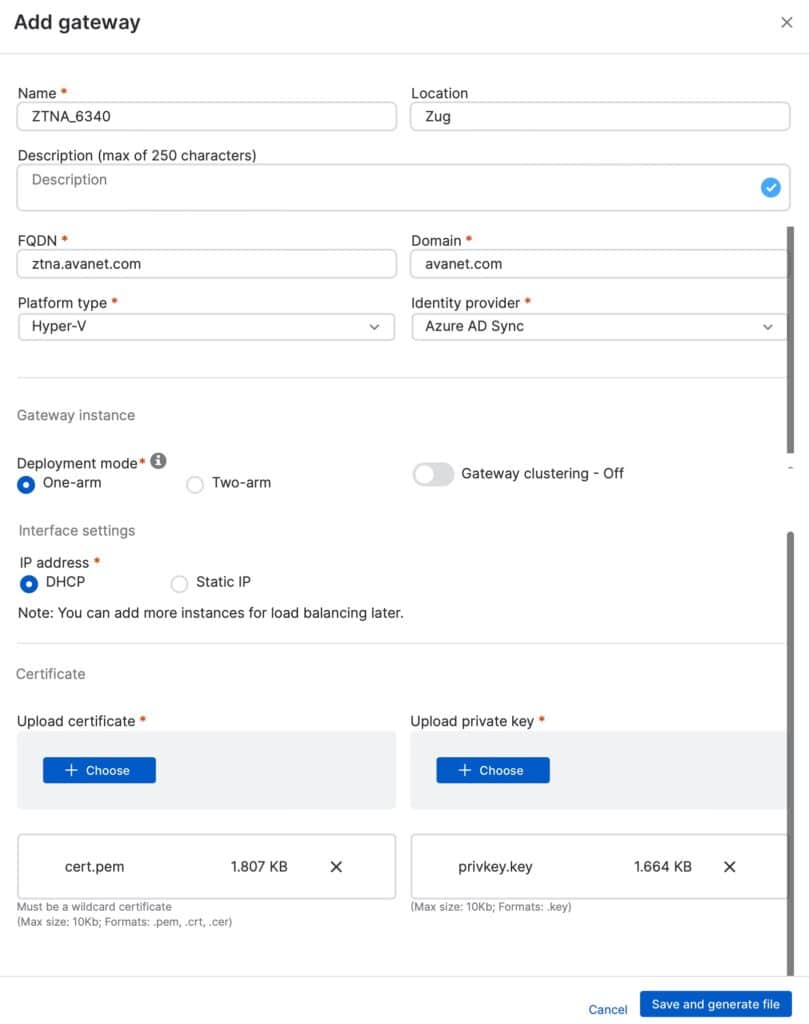
Mode: On-premise gateway or cloud gateway. In my case, I use the on-premise gateway. The ZTNA Cloud Gateway is intended for a ZTNA as a Service from Sophos. No DNAT rule is used here to direct the traffic to the gateway; instead, the Cloud Gateway reports to Central.
Name: Simply a name with, for example, the location or hostname of the gateway.
Location: If you have multiple locations, you can optinally store this.
FQDN: DNS name pointing to the public IP of the firewall, which in turn provides a DNAT (https / 443) rule on the ZTNA gateway.
Domain: Results from the domain name which one uses.
Platform type: Here you can choose between VMware ESXi, Hyper-V and Amazon Web Services (AWS).
Identity provider: Select the previously added provider, in my case Azure AD.
Gateway Instance Deployment mode: One-arm is used if a DNAT rule is created afterwards, Two-arm if the ZTNA gateway has an interface in the LAN as well as in the WAN.
IP address: This should be self-explanatory.
I use DHCP here and reserve an IP on the DHCP for the ZTNA gateway.
Certificate: Wildcard certificate of the domain specified above.
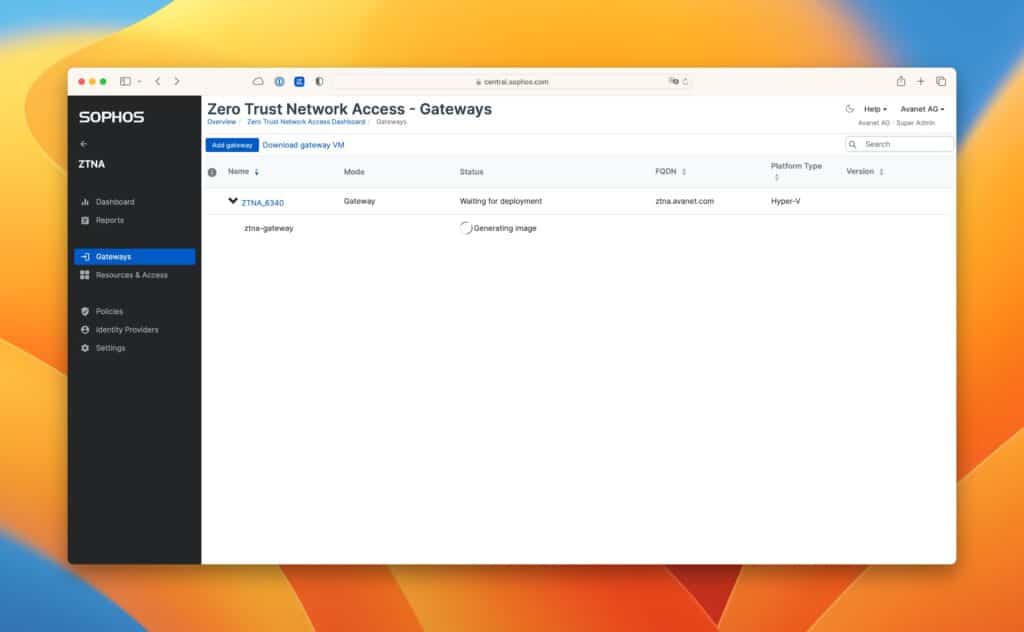
After saving, an ISO image is created with the stored information, which can be downloaded as shown in the screenshots. This ISO image is now used as boot ISO for the VM.
Depending on the performance of the host, the first start and the registration at Central takes up to 30 minutes. As soon as the gateway reports to Central, you can then still accept this and this step is thus also completed.
More information in the Sophos KB: Set up a gateway