
Sophos Firewall Feature Request 2024
We ourselves work with Sophos Firewall on a daily basis and our customers also give us feedback on which security and operating functions are missing. We have compiled a detailed list based on this experience and feedback. We are now summarizing this feedback in the Sophos Firewall Feature Request.
Sophos Firewall Feature Request
Let’s Encrypt support
This is the most frequently requested feature, for which many have been waiting for over three years. This feature will finally be included in version 21, which is due to be released in October.
Rename objects
Unfortunately, it is currently not possible to rename certain things on the firewall, here are a few examples:
- Site-to-site IPsec connections
- Zones
- DHCP Server
- IPS rules
This function would be extremely useful for keeping configurations clearer and more organized.
If you want to rename a side-to-side VPN connection, for example, you have to delete it and create a new one just to change the name.
Responsive GUI
With the update to version 20, the GUI has been slightly optimized for widescreen monitors in order to reduce the white space. This was already a very frequently requested Sophos Firewall feature request.
Nevertheless, our customers want a fully responsive interface that also looks good on tablets and mobile devices. There is still room for improvement, especially on small monitors and with 4K resolution.
Backend performance
The GUI is slow, especially with the smaller firewall models, the devices often react very slowly, especially when saving firewall rules. There is still a lot of potential for optimization here to improve the user experience.
For example, saving a firewall rule on an XGS 126 with SFOS v20 takes too long.
The interfaces take a similar amount of time to load and the dashboard takes around twice as long.
Grouping NAT rules
It is possible to group firewall rules in order to organize them better. However, this function is missing from the NAT rules. Again, a grouping option would be a useful Sophos Firewall feature request.
Clone NAT rules
While the function for cloning firewall rules is already available, this useful option for NAT rules is missing. It would be very beneficial if NAT rules could also be cloned in order to make configurations faster and more efficient. This is a common Sophos Firewall feature request from our customers.
Customize and save log viewer
The log viewer allows you to add or remove columns in order to display the logs more clearly. It would be helpful if these settings could be saved so that you have your preferred column views the next time you open the log viewer.
Integrated speed test
An integrated speed test that can be carried out directly via the firewall is at the top of many users’ wish lists. Other manufacturers already offer these functions, which make it possible to carry out speed tests via various interfaces directly from the firewall or to schedule them on a time-controlled basis.
Hide warning messages in the dashboard
Warning messages or alarms are displayed in the dashboard, but they cannot be hidden. Many users would like to be able to mark these messages as seen so that they are not displayed permanently.
Import several objects at the same time
The ability to import several objects at the same time would be a valuable addition. IP lists can currently be imported, but URL lists or multiple networks cannot. This function would contribute significantly to efficiency, especially for exceptions in Microsoft services where many networks or URLs need to be listed.
Links to firmware release notes
For firmware updates for RED or Access Points, there is currently only an “Install” button in the backend, without detailed information on the changes being available. This presents administrators with the problem that they do not know what changes or improvements the new firmware will bring. This is particularly problematic as there is no option to roll back if problems occur after installation.
A direct link to the release notes would therefore be a very practical Sophos Firewall feature request. This allows you to check the changes before installation and better assess the risks or benefits of the update. Currently, you have to search for details in the Sophos Community, which again takes time.
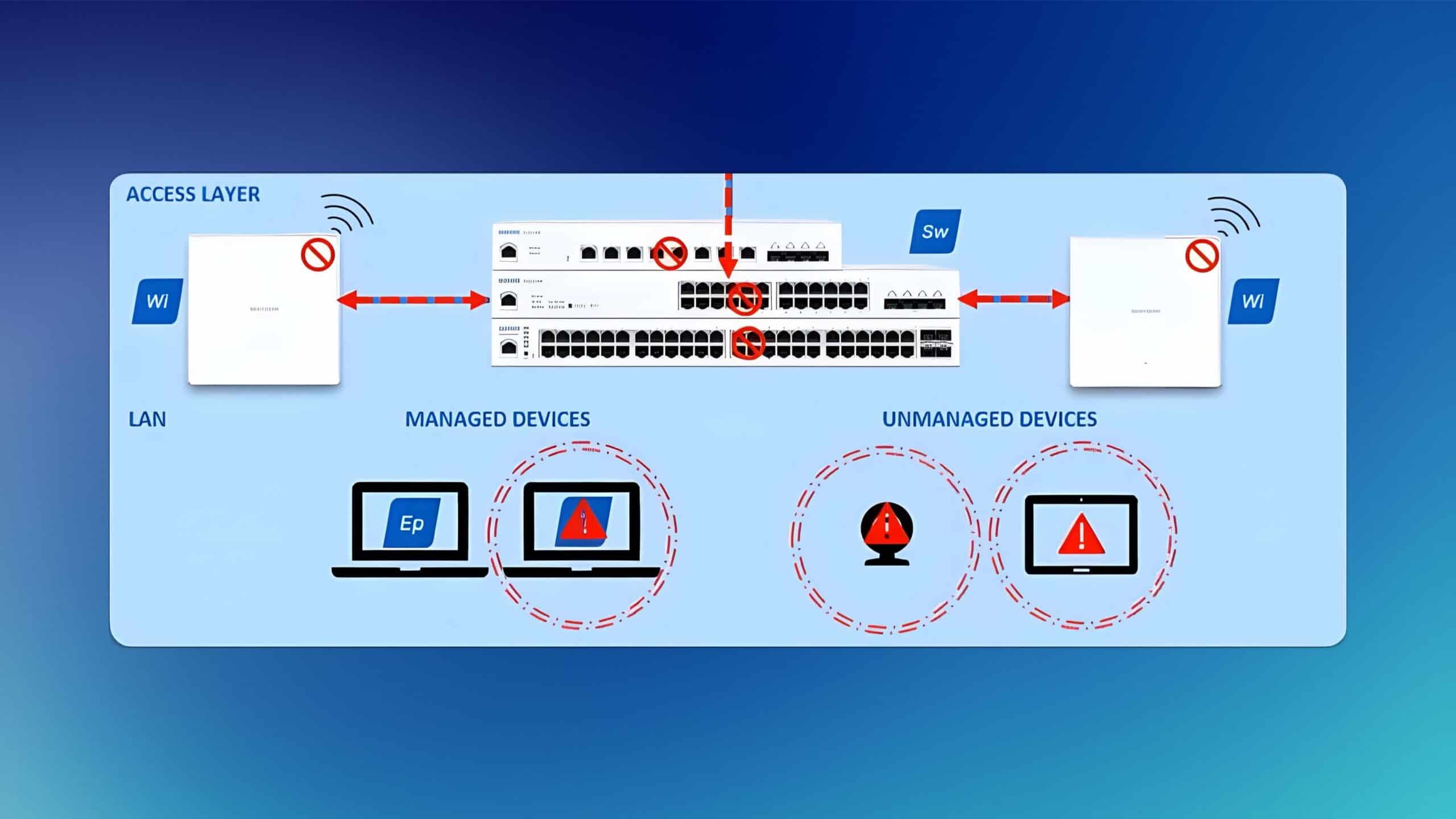
Auto Block attack
A related function that is easy to imagine is the password security mechanism, which triggers a temporary lockout if too many login attempts fail. This mechanism is familiar to most administrators and is already used with the Sophos Firewall.
This mechanism blocks the login after a certain number of failed attempts and blocks access for a set period of time. A similar function for the firewall would be extremely useful for automatically blocking IP addresses if several suspicious activities are detected within a short period of time.
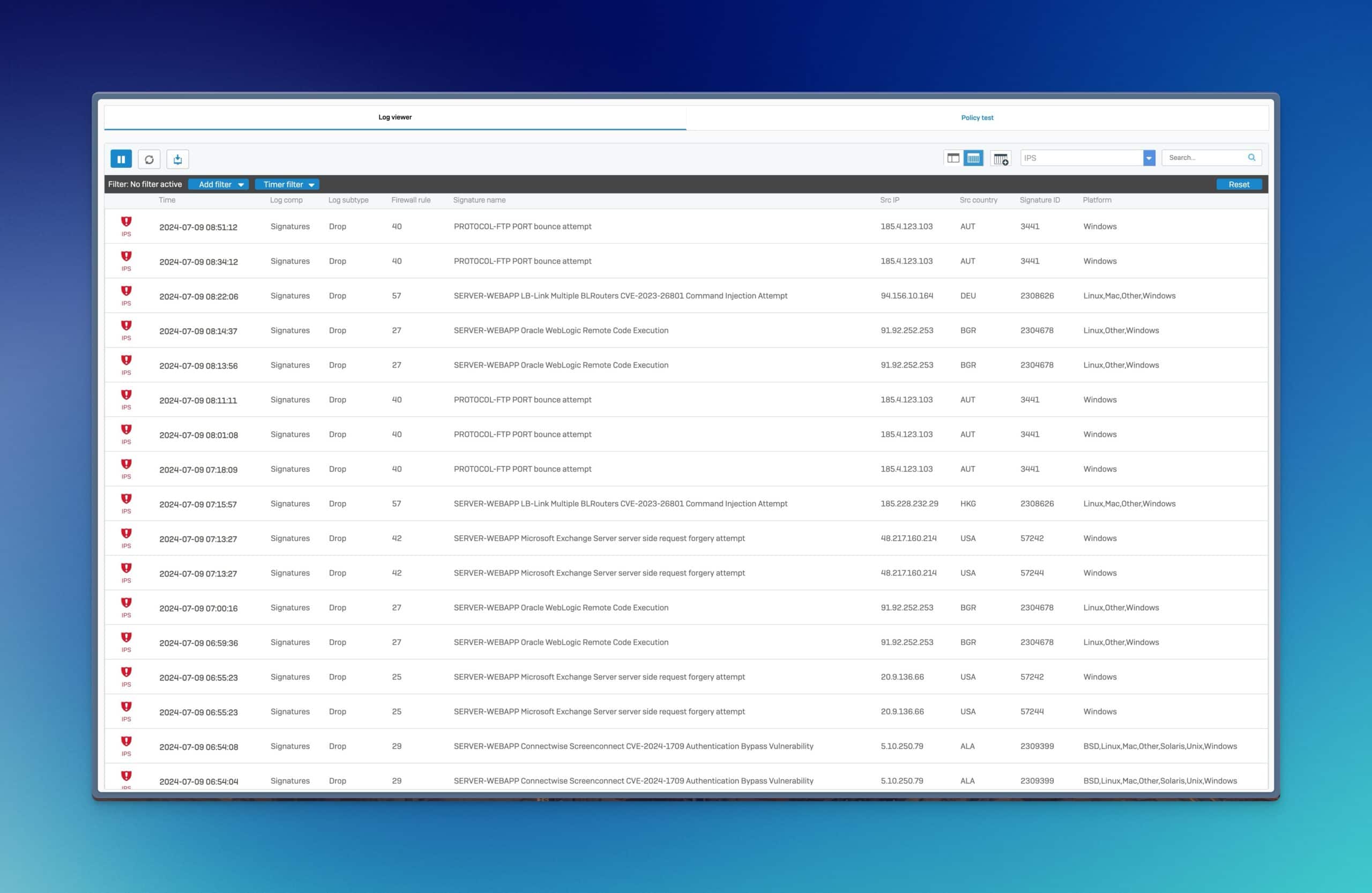
A similar method is also used by Fail2Ban, a program that checks logs and blocks IP addresses that show certain predefined patterns of attacks or suspicious activity. Fail2Ban thus protects systems against brute force attacks and other threats by automatically blocking attackers.
It is obvious that such an automatic blocking function would also be extremely useful for the Sophos Firewall. Currently, the Intrusion Prevention System (IPS) recognizes suspicious activities and blocks them, but the attacker can continuously repeat his attempts. Any suspicious activity triggers a notification and the administrator must intervene manually to block the IP address.
An autoblock mode, where the administrator can set an IP address to be blocked for 15 minutes, an hour or even longer, would significantly increase efficiency and security. If the firewall detects several suspicious activities from a certain IP address within one minute, it would make sense to automatically block this IP for a certain period of time. The administrator could maintain the blacklist at any time and remove the address if necessary.
The introduction of such an autoblock module would protect the firewall even more effectively against repeated attacks and at the same time reduce the administrative workload for the administrator.
Then it would once again be a battle of machine against machine, because at the moment most attempted attacks are carried out by bots or machines. However, there is an administrator behind the Sophos Firewall who has to deal with such events manually in order to prevent further requests.
Bad IP Blocker Feeds
In the upcoming firewall version 21, it should be possible to implement predefined lists to block access to dangerous IP addresses. This means that if someone internally tries to access an already known dangerous IP, this access is automatically blocked. In future versions, these lists will be supplemented by third-party providers. Unfortunately, however, only outgoing connections are checked against these lists.
A great extension would be to add feeds to the firewall that contain IP lists, in particular to block known dangerous IPs for incoming connections. This could apply to NAT rules, VPN requests, user portal requests and other services.
The web application firewall already has a similar function called “Block clients with bad reputation”, which does the following:
It blocks clients that have a bad reputation due to real-time blackhole lists (RBLs) and GeoIP information. Skipping remote queries for clients with a poor reputation can improve performance. For RBLs, Sophos Firewall uses the Sophos Extensible List (SXL) and SORBS. She uses Maxmind for GeoIP. The Sophos Firewall blocks clients that fall into the categories A1 (anonymous proxies or VPN services) and A2 (satellite ISPs).
The wish would therefore be that you could subscribe to your own RBL feeds, for example from well-known manufacturers or from GitHub.
Such an extension would significantly increase the security of the firewall and its services by effectively protecting not only outgoing but also incoming connections against known threats.
Deactivate wireless service
Although there is an option to deactivate the wireless service, this is displayed as an error. You will then see a warning message in the dashboard:
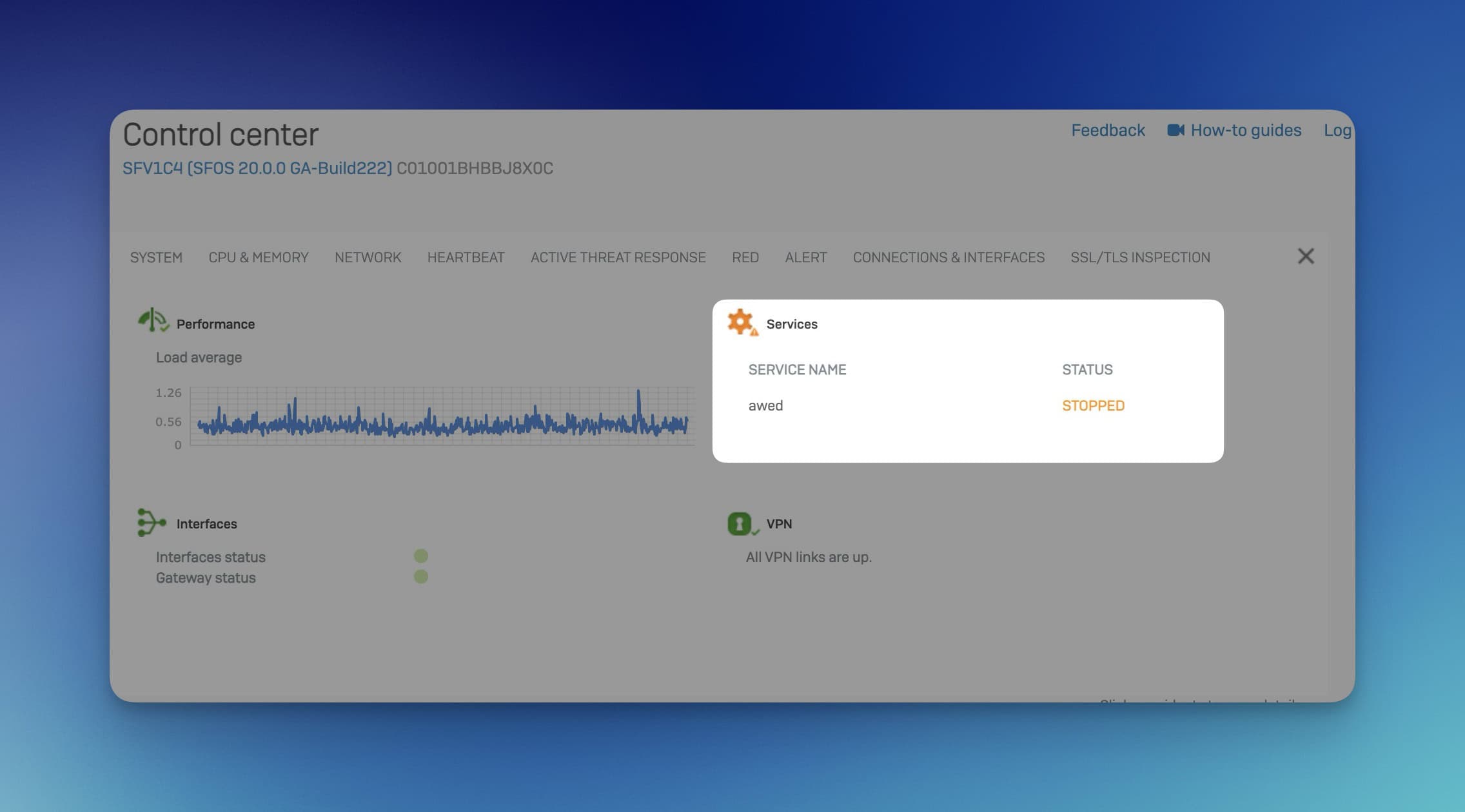
This means that even if the administrator deliberately deactivates the service in order to conserve resources or for other reasons, the firewall interprets this as a problem and issues an error message. It would therefore be desirable to have a way of deactivating the wireless service without this appearing as an error in the dashboard.
Feedback to us
In this post, we have compiled the most common Sophos Firewall feature requests that we have collected over the last few months. We have taken into account both the wishes of our customers and the functions that would help us to set up and maintain the numerous customer firewalls more efficiently.
However, if you have any further suggestions or requests, please send us your feedback using the contact form. We will update this blog post regularly to reflect the latest needs and requirements.
Roadmap is also no guarantee
You should never buy a product just because a manufacturer promises that the function you want will be added via an update.
Sophos is no different. The roadmap is about as reliable as the weather forecast, horoscopes or the behavior of cats. Features are added and removed, services are presented at the roadshow or things are written in the product data sheets with the reference (coming soon), but that doesn’t mean anything yet! I could write a separate post about the Sophos announcements that didn’t materialize. Plus, Sophos is unfortunately not one of the manufacturers that listens to the users and develops the functions accordingly, that would be completely absurd. It’s better to run after the next hype from the Gartner analysts or what the shareholders want to hear, or look at the competition.
I think that should make everything clear and I have already nipped false hopes in the bud.



