Set up Sophos Firewall as NTP server
The title is, technically speaking, incorrect, as the Sophos Firewall does not run an NTP service. However, this can be solved with a NAT rule so that the Sophos Firewall takes care of all NTP requests and the gateway IP can still be specified as the NTP server on the client or server.
Create NAT NTP rule
First, I create a NAT rule that takes care of the NTP protocol.
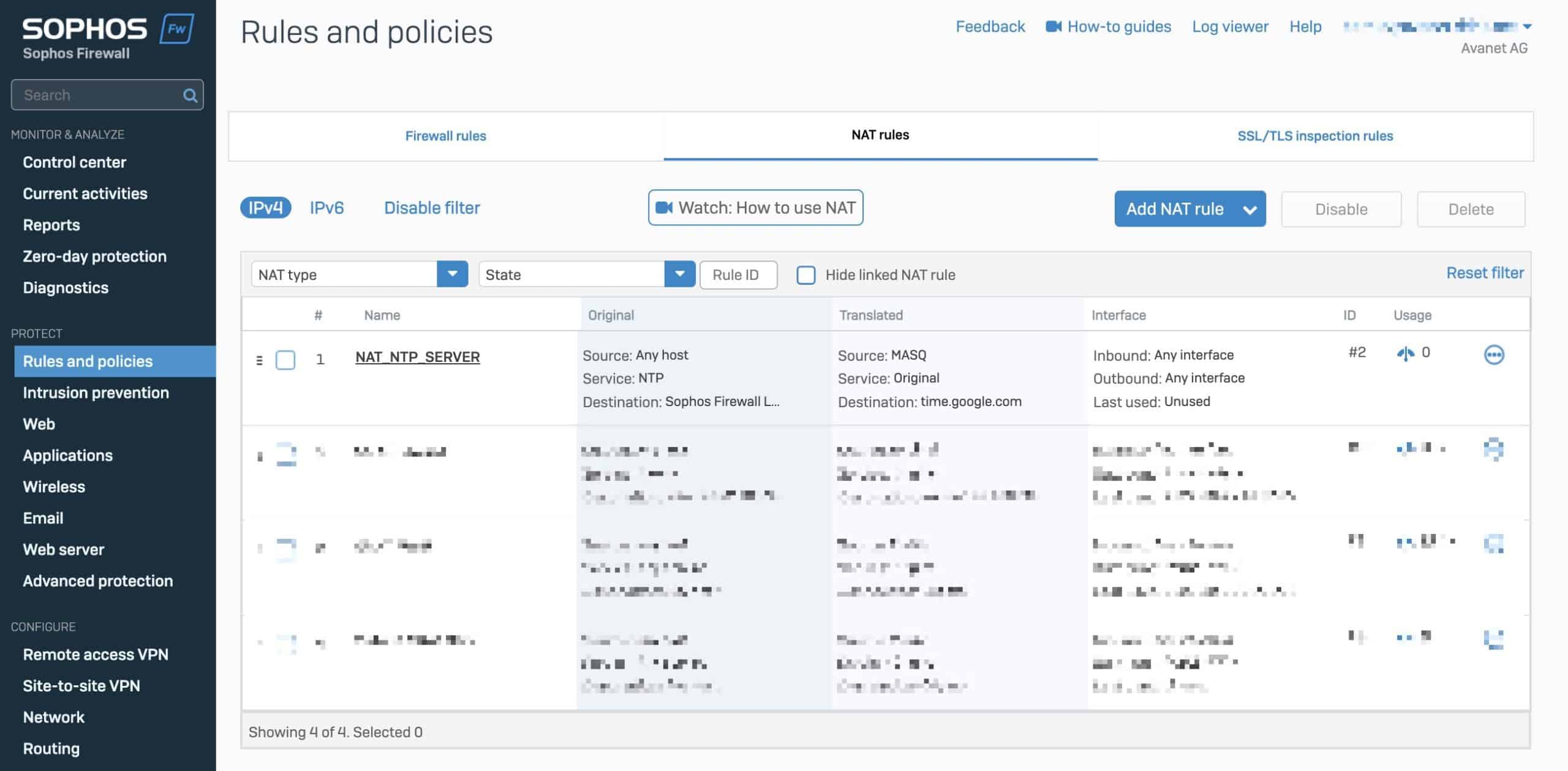
The NAT rule now defines for which local networks the Sophos Firewall should answer NTP requests.
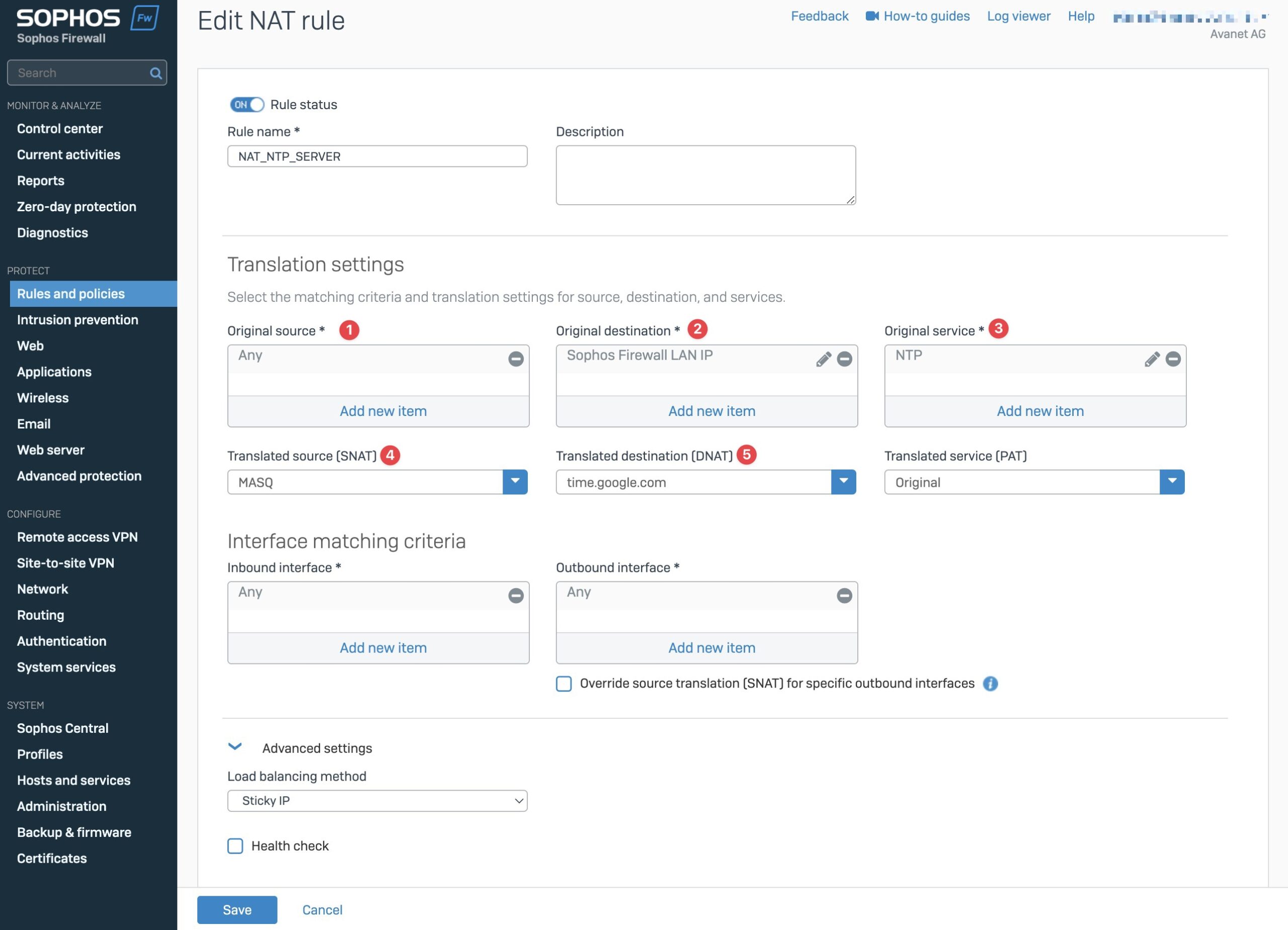
1. Original Source
The networks or individual IP addresses that are to use this NAT rule are entered here. For example, 192.168.33.0/24 or ANY, if every request is to be processed.
2. Original Destination
Here you list all IP addresses that the Sophos Firewall should listen to. For example, the gateway address: 192.168.12.1 or ANY, if every request is to be considered.
3. Original Service
NTP is specified as the protocol, which is already a predefined service on the firewall.
4. Translated Source (SNAT)
The firewall should perform IP masquerading and therefore we select MASQ as the value here.
5. Translated destination (DNAT)
Here we enter the NTP server address to which the firewall should send all time requests. I use the FQDN time.google.com here or pool.ntp.org is also popular.
Inbound Interface
In addition, you can also store the local interfaces, for example, so that you are sure not to answer any WAN requests. I leave it at ANY and solve this afterwards via the firewall rule.
Firewall rule for NTP service
To allow the traffic of the NAT rule, you need a firewall rule, which you now create.
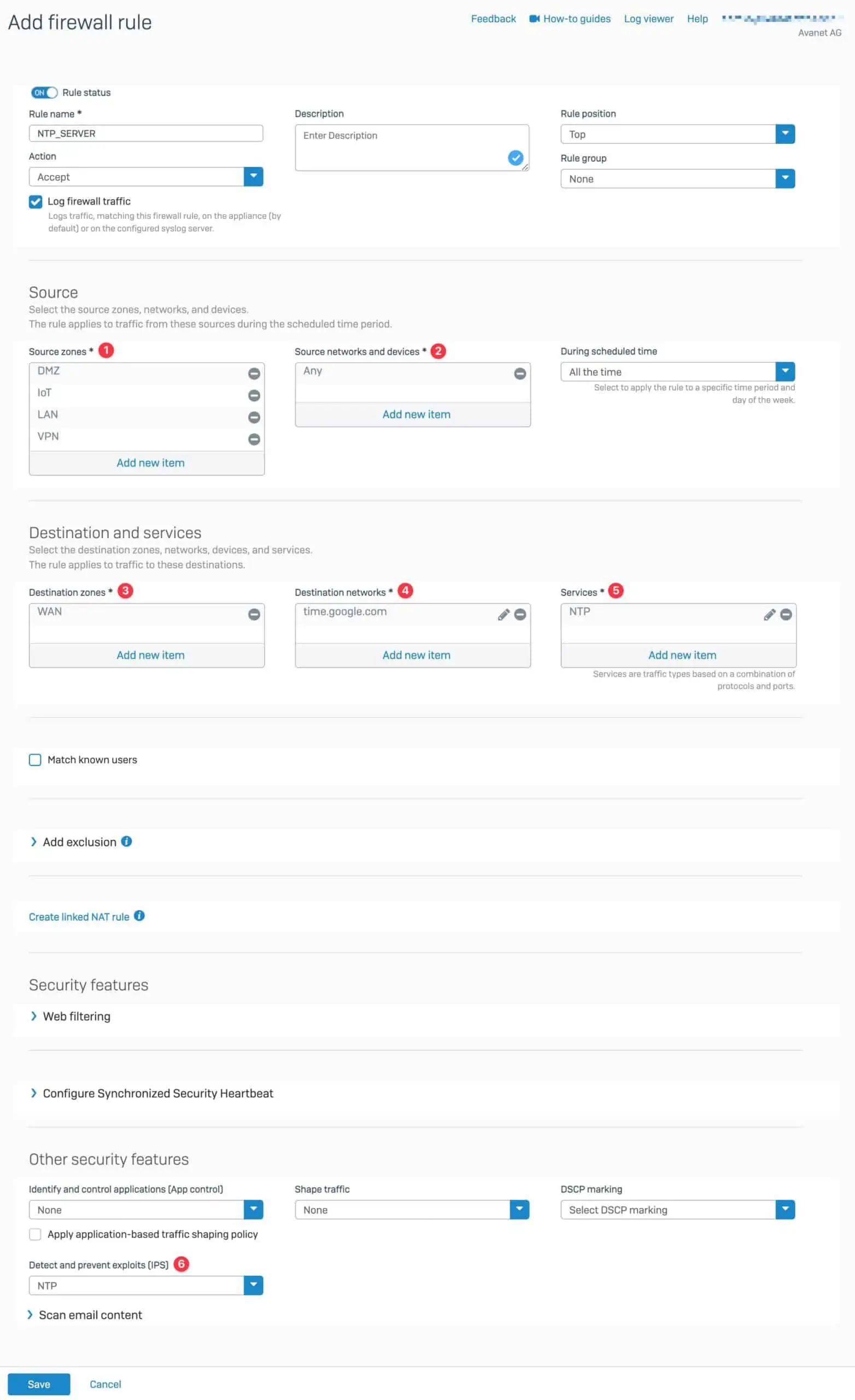
1. Source Zones
Here we list all source zones, such as LAN. What we do not want to see here is the WAN zone, as we do not want to provide an NTP server for the Internet here.
2. Source Networks and Devices
Here we can list the same networks as in the NAT rule at point 1. original source. Since I solve this here via the zone, I leave it at ANY, but you can of course also store both zone and source networks.
3. Destination Zones
Since our time server is on the Internet, I choose the WAN zone here.
4. Destination Networks
I have defined time.google.com as the NTP server in the NAT rule. That’s why I choose this FQDN here, but I could leave it at ANY, as this is already defined in the NAT rule. However, I like to see immediately in the firewall rule where the traffic is going.
5. Services
As with the NAT rule, we use the predefined protocol NTP.
6. Detect and prevent exploits (IPS)
You have the firewall because you also want to bring some security to the network. That’s why we also provide an IPS rule for the NTP traffic. For this, I simply created an IPS rule with the Smart Filter nat.
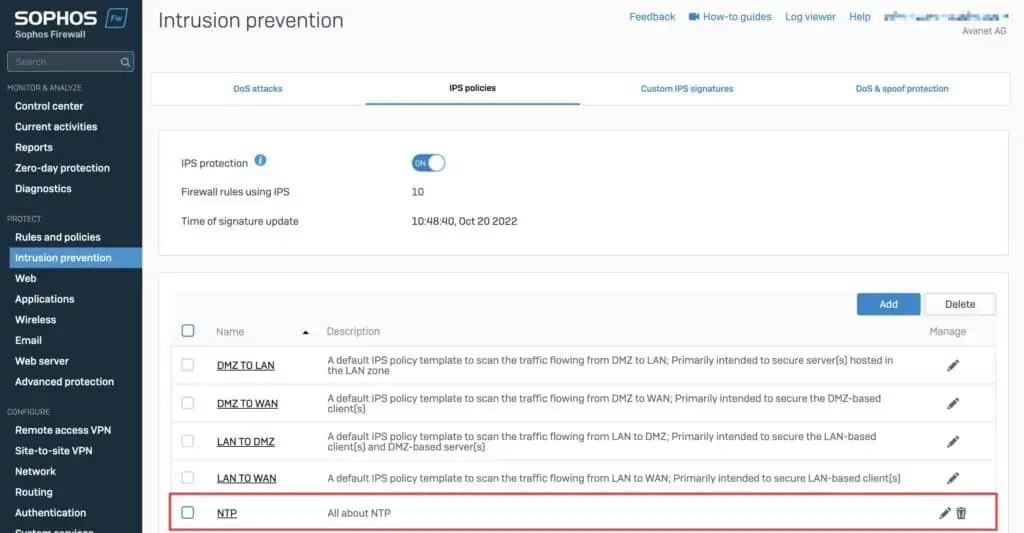
⚠️ The IPS (Intrusion Prevention) function requires a Network Protection licence.