Sophos Firewall – IPsec remote access timeout after 4 hours
This article explains why an IPsec remote access timeout occurs after 4 hours and how this problem can be solved.
For IPsec Remote Access, a timeout of 4 hours is set by default on the Sophos Firewall. In this case, the Sophos Connect Client loses the connection to the firewall and the user must re-establish the connection.
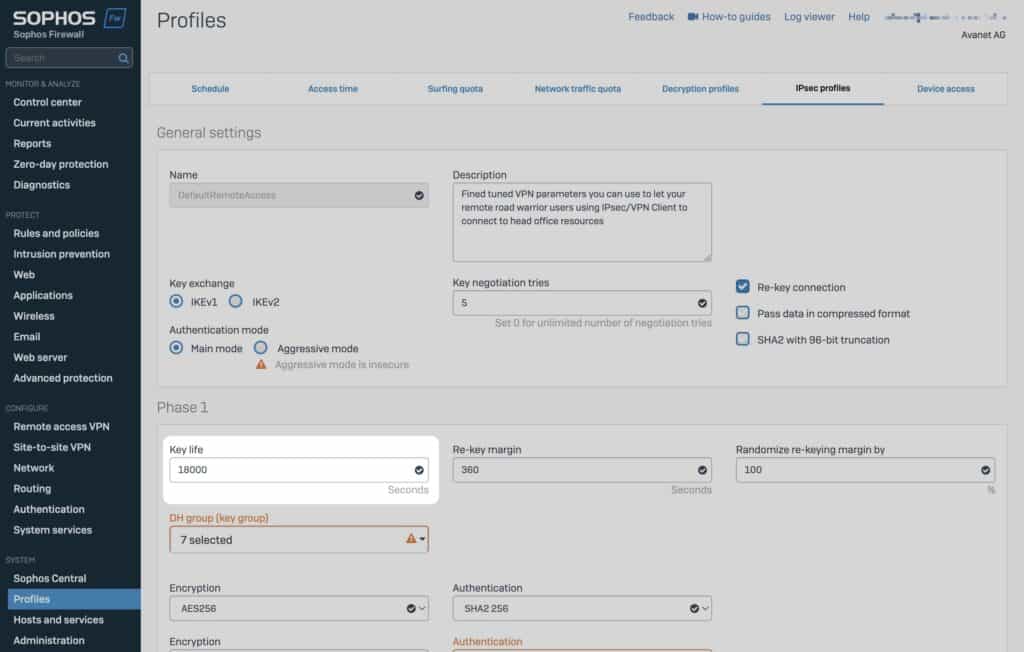
If the Sophos Connect Client has configured users with a one-time password (OTP), the user is prompted to enter a new OTP every 4 hours by default. This is because the Sophos Connect Client uses the DefaultRemoteAccess policy, which can be changed via the graphical user interface. The default value for ikekeylife is 18000
Sophos Firewall Log
These errors in the VPN log show that the connection was interrupted due to an expired IKE key. The invalid SPI (Security Parameter Index) refers to an expired or invalid IKE phase 1 session.
VPN 2023-12-12 06:33:48 IPSec Deny Received IKE message with invalid SPI (421B67D8) from the remote gateway. 18050
VPN 2022-12-12 06:33:47 IPSec Deny Received IKE message with invalid SPI (13B56627) from the remote gateway.18050
VPN 2022-12-12 06:33:46 IPSec Deny Received IKE message with invalid SPI (EDA41714) from the remote gateway.18050Customize IPsec VPN timeout via Sophos Firewall GUI
In the VPN profiles you will find the DefautlRemoteAccess certificate and can clone it and adjust the value accordingly.
Then you just have to select the new certificate in the Remote Access IPsec settings and distribute the new config to the users.
Adjust IPsec VPN timeout via Sophos Firewall console
With an IKE_SA lifetime value of 18000, IKE_SA re-encryption occurs approximately every 4 hours and re-authentication also occurs along with IKE_SA re-encryption, prompting users to enter a new OTP.
If the customer requirement is that the user should be prompted to enter a new OTP every “n” hours, then use the following equation to determine the appropriate ikekeylife value if n=10 (i.e. 10 hours)
ikekeylife = (n +1) * 3600
ikekeylife = (10 +1) * 3600 = 39600
ikekeylife = 39600Note: The maximum value for “n” should not be greater than 23.
Connect to the Sophos Firewall via SSH, e.g. via Putty, and enter 5 and then 3 to access the Advanced Shell.
psql -U nobody -d corporate -c "update tblvpnpolicy set ikekeylife=39600 where policyid=5;"Afterwards, you only have to restart the IPsec VPN service on the firewall and redistribute the config file to the clients.