Sophos Firewall v20 MR1: New features and improvements
Sophos Firewall v20 MR1 brings a host of new features and enhancements that further improve the security and performance of the firewall. Here are the most important new features in detail:
⚠️ Important for all RED 15 and RED 50 users who have not yet upgraded to SD-RED 20 or SD-RED 60. The message that the REDs are End of Life has been displayed on the firewall for some time. After this update, the old RED models are still visible in WebAdmin, but no longer connect to the firewall.
Content
Automatic language recognition at login
Immediately after booting with the new Sophos Firewall v20 MR1 firmware, you will see the first change. Everyone can decide for themselves whether it’s good or bad, but as far as I’m concerned it’s more the latter.
The language for the admin portal is automatically determined based on the browser settings. This is then also saved as a cookie.
Improved firewall security and access control
The new version gives you even finer control over which services are accessible in the WAN. This significantly improves the security of your firewall. What is not visible cannot be attacked.
The setting options for IPsec VPN and the RED are new additions:
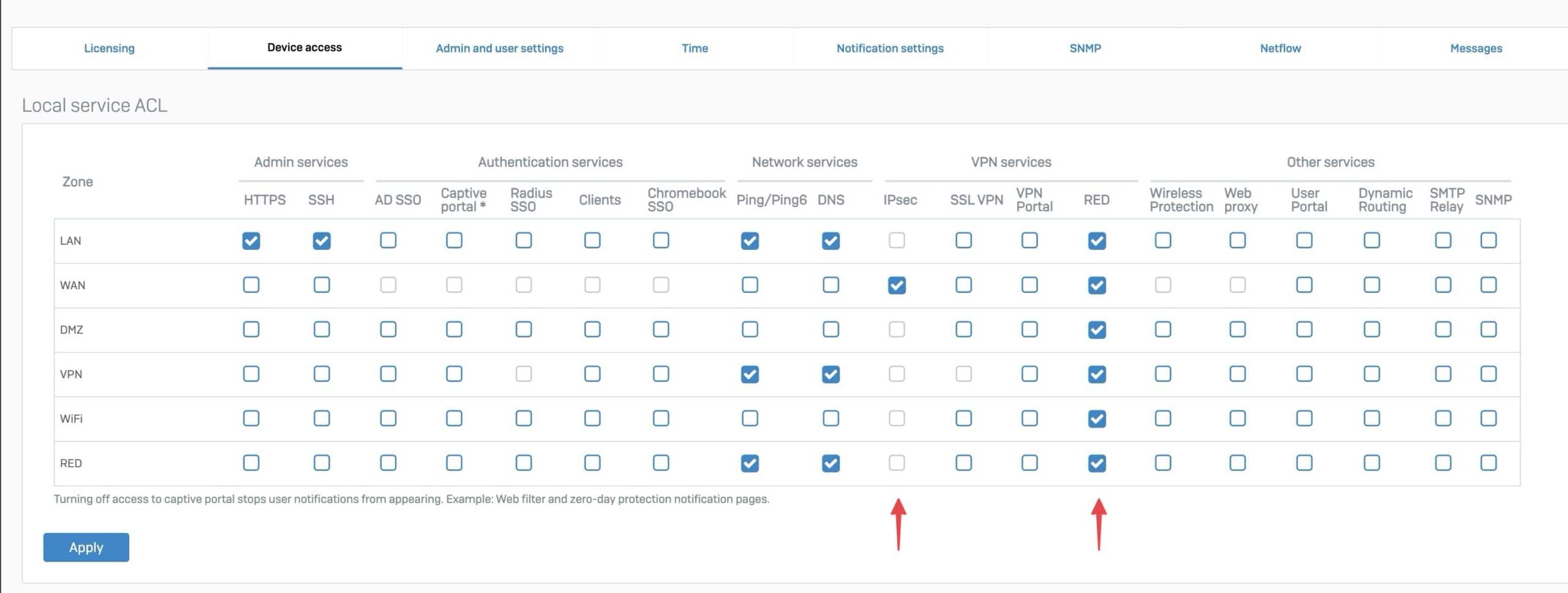
New services in the Local ACL exception list
However, there can still be a large attack surface behind a zone and it is therefore advisable to define access even more precisely in the “Local service ACL exception rule”.
The following services have been added to the exception list: AD SSO, Captive Portal, RADIUS SSO, Client Authentication, Wireless, SMTP, RED, IPsec and last but not least Chromebook, although I have never seen a Chromebook except on YouTube 🤷♂️.
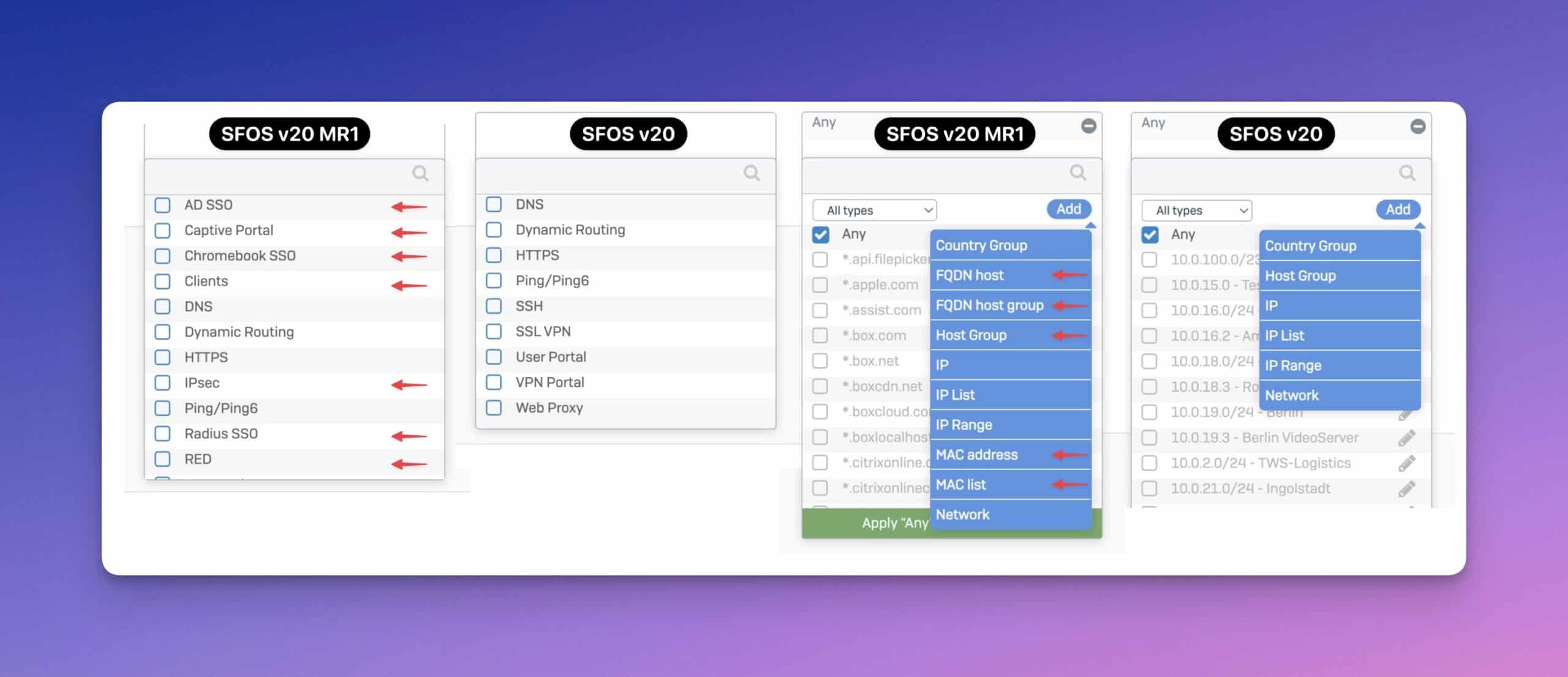
More flexible access control exceptions
The new version of Sophos Firewall v20 MR1 significantly improves the flexibility of access control exceptions and adds three key objects.
- Support for FQDN hosts: You can now use fully qualified domain names (FQDNs) in the exception rules. This allows for more precise control over traffic by controlling access to specific domains based on their names instead of just IP addresses. I was looking forward to this feature (which was available on the UTM 🤐) for a long time.
- Host groups: The ability to define and use host groups provides enhanced flexibility in managing access rules. You can combine several hosts into a group and then use this group in your exception rules.
- MAC addresses: In addition to IP addresses, MAC addresses can now also be included in access control exceptions. This provides an additional level of control, particularly useful in networks with many dynamic or changing IP addresses.
Zero-touch deployment
Zero-touch deployment is an advanced feature of Sophos Firewall v20 MR1.
In many cases, we at Avanet replace the existing firewalls 1:1 with new ones, and it is important that this is done quickly and with minimal disruption. We normally pre-configure the device in our office and then send it to the customer, where it just needs to be replaced.
In the past, Zero-Touch Deployment required a USB stick to transfer the configuration file to the firewall. With the new version, however, this is no longer necessary, as the entire configuration can be done via Sophos Central.
Here are the steps and the improvements in detail:
- Enter serial number: The serial number of the new firewall is entered in Sophos Central. This is used to identify and initialize the firewall.
- Set basic configuration: A basic configuration is defined which is used when the firewall is started for the first time. This includes important settings such as time zone, firewall host name and network configurations for LAN and WAN.
- Establish an Internet connection: The firewall is simply connected to the network on site, whereby it automatically connects to Sophos Central and downloads the predefined configuration.
- Activate firewall management: After connecting to Sophos Central, the firewall is automatically configured and ready for use. Administrators can then make further settings and fine-tuning directly via Sophos Central.
This method significantly reduces the time and complexity of the installation. In addition, the firewall can be used as soon as it is connected to the Internet, which speeds up the entire process.
Advantages of zero-touch deployment
- Fast deployment: Ideal for locations where there is no IT staff on site. The firewall can be configured and made ready for use as soon as it is connected to the network.
- Centralized management: All configuration steps are carried out via Sophos Central, which enables uniform and consistent management.
- Minimal interruptions: As the configuration is defined in advance and applied automatically, downtime is minimal, which is particularly beneficial in business-critical environments.
- Simple adjustment: After the initial configuration, further adjustments and settings can be made centrally without the need for a technician to be on site.
With Zero-Touch Deployment, Sophos offers an efficient solution for deploying and configuring firewalls that saves time and maximizes network availability.
Download log files for troubleshooting
With Sophos Firewall v20 MR1, it is now possible to download individual log files directly from the firewall. This function simplifies troubleshooting, as it is no longer necessary to access the firewall via an SSH connection to obtain the necessary data.
Under the main menu item Diagnostics you will find the option Troubleshooting Logs. Here, administrators can search for specific logs and select several logs at the same time. Sophos Firewall then offers a ZIP file for download that contains all the selected logs. These files can be opened and analyzed on a local client.
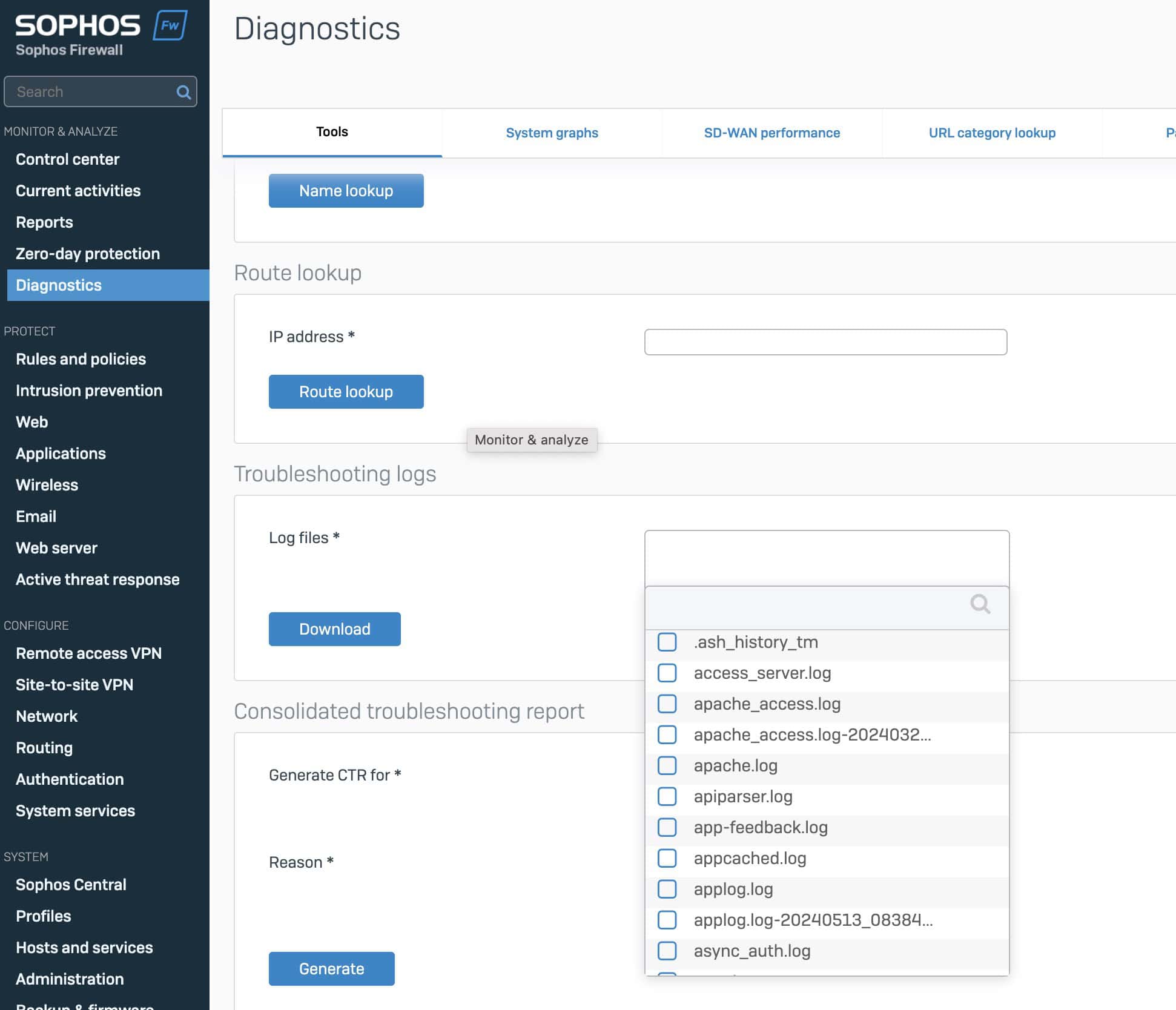
Each site-to-site IPsec connection and individual RED connection receives its own log. This enables a detailed and specific analysis without having to resort to cumbersome methods. This makes firewall management and maintenance more efficient and user-friendly.
Description fields for objects
All objects under “Host & Services” now have a description field. This includes IP hosts, IP host groups, MAC addresses and other network objects. The option of adding a detailed description to each object significantly improves the documentation.
This function makes it possible to store important information directly in the firewall. For example, when creating a new IP host, you can add a description that explains the purpose and use of the host. This is particularly useful if several administrators manage the firewall or if precise documentation is required.
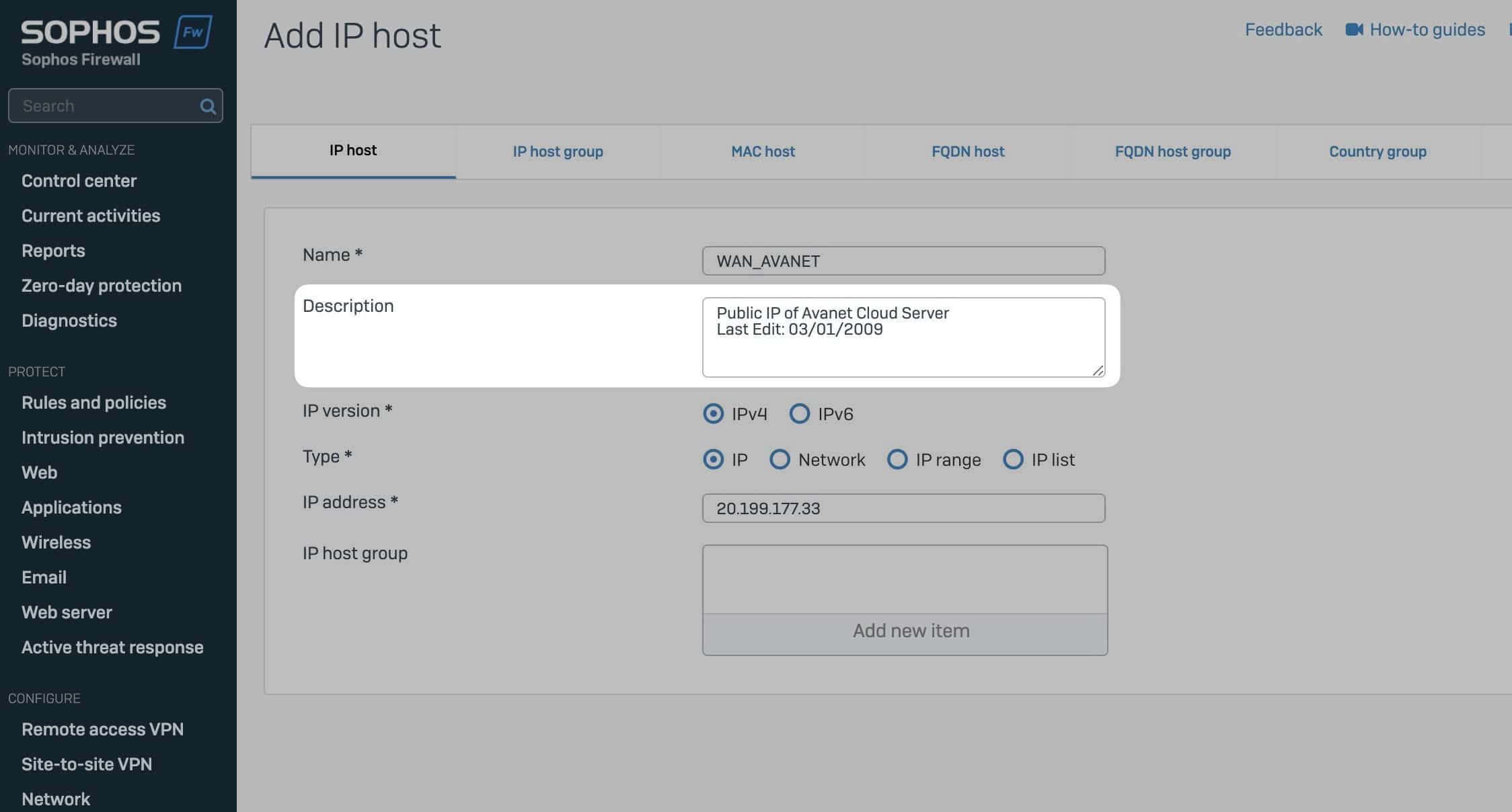
A description could also contain links to further information, such as a knowledge base or a PDF document that provides specific details about the object in question. This increases traceability and facilitates future administrative tasks. This means that a service port that is only used for a specific application can be provided directly with relevant information and context, which significantly increases efficiency and clarity in network management.
The description is also indexed to enable a search.
Generative AI Firewall Assistant
Today, you’re simply no longer cool as a company if you don’t mention AI. A few years ago it was still blockchain.
A new generative AI-powered Sophos Assistant is integrated to help you manage your firewall. You can ask the assistant any question in simple language and receive instructions and links to helpful resources.
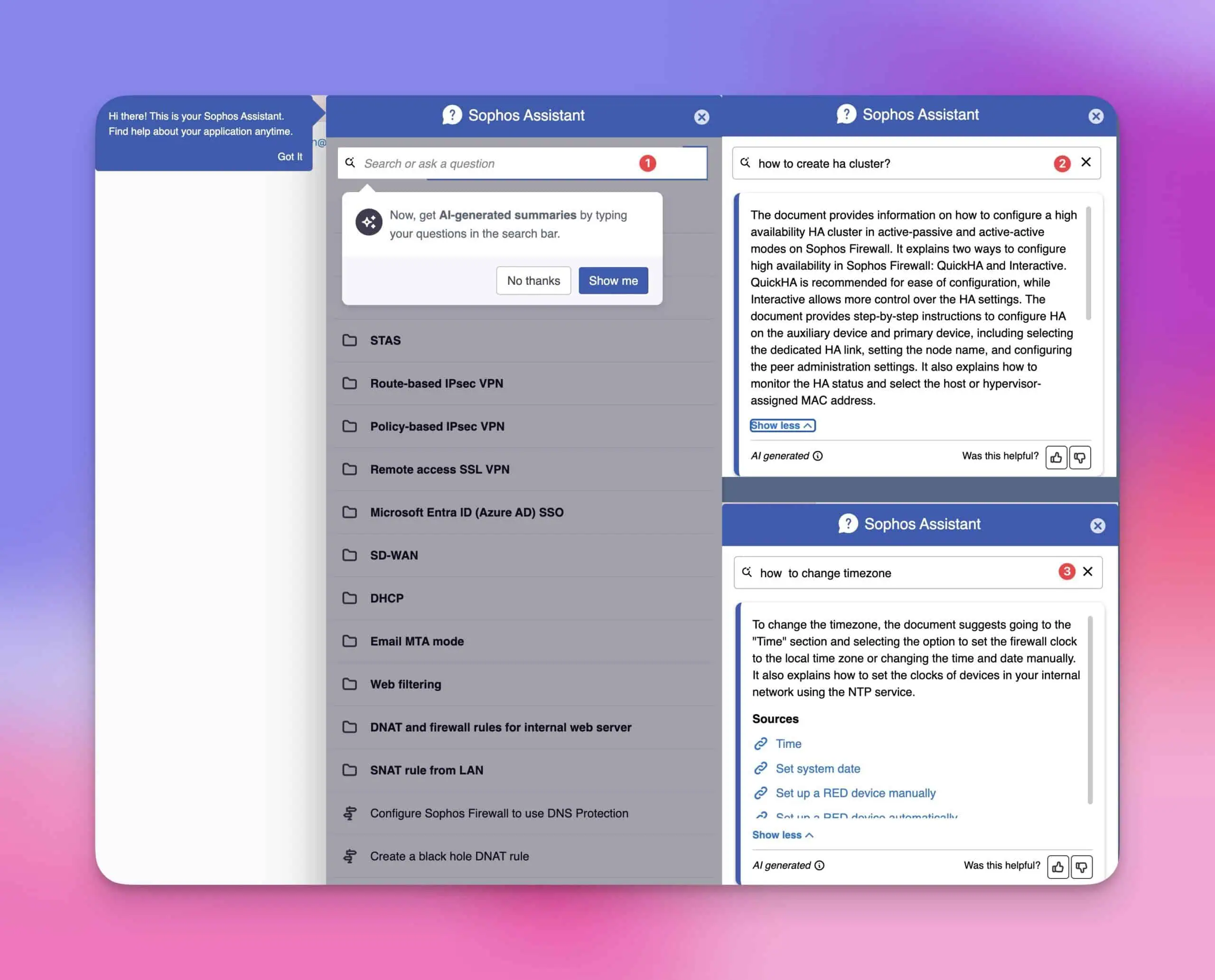
Not bad for a first version, but I think we imagine AI to be different than just a slightly better search?
OpenVPN Upgrade to v2.6.0
The OpenVPN component of the Sophos Firewall has been updated to version 2.6.0. This improves security and performance for SSL VPN. Site-to-site SSL VPNs with older versions are no longer supported. It is recommended to upgrade to v20.0 MR1 or to use alternative VPN solutions such as IPsec.
In addition, the latest version of the Sophos Connect Client (v2.3) can be downloaded via the VPN Portal:
- Install Sophos Connect SSL VPN Client (Windows) – SFOS
- Sophos Community: Sophos Connect 2.3 Update Released
- Sophos Commuinity: Sophos Connect news and release notes
Important notes on SSL VPN compatibility
By upgrading to OpenVPN 2.6.0 in this version, SSL VPN tunnels are no longer established with the following clients and firewall versions:
- SFOS v18.5 and earlier versions: Site-to-site SSL VPNs can no longer be established. It is recommended to update all relevant firewalls to v20.0 MR1 or use site-to-site IPsec or RED tunnels.
- Legacy SSL VPN Client: Remote Access SSL VPN tunnels are no longer established with the outdated SSL VPN Client. Use the Sophos Connect Client or third-party clients such as the OpenVPN Client.
- UTM9 OS: Site-to-Site SSL VPNs can no longer be established between UTM9 OS and SFOS v20.0 MR1. It is recommended to migrate these devices to v20.0 MR1 or use site-to-site IPsec or RED tunnels.
Improvements to SD-WAN and VPN
The new version of Sophos Firewall v20 MR1 brings important SD-WAN and VPN improvements that significantly increase both reliability and performance.
- Minimal traffic interruptions: Gateway availability during HA failover and device restarts has been improved by a factor of four. This means that if a gateway fails or a device restarts, interruptions in data traffic are significantly minimized, resulting in a more stable network connection.
- New OpenVPN 3.0 Client: The new OpenVPN 3.0 Client for Remote Access SSL VPN is now available for download via the VPN Portal. This client offers enhanced security features and greater compatibility with different operating systems, simplifying the setup and management of VPN connections and improving the user experience.
- IPsec Phase-1 IKEv2 support: Support for GCM and Suite-B ciphers has been added, improving interoperability and throughput for IPsec connections. These modern encryption methods ensure more secure and efficient data transmission between network devices.
- DHCP Busybox improvements: The default lease time for DHCP has been set to 30 seconds to eliminate WAN connectivity issues. Shorter lease times mean that IP addresses are assigned and renewed faster, resulting in a more stable and reliable network connection, especially in environments with frequently changing connections.
Install Sophos Firewall v20 MR1
To install the latest firmware version, an Enhanced Support license is required, unless the firewall has just been purchased and still has an evaluation license: Sophos Firewall updates will no longer be free in the future
This guide describes how to install the latest version on your firewall and download the image: Updating the firmware on Sophos Firewall (Firmware Update)
More information about the release can be found in the Sophos Community – Sophos Firewall OS v20 MR1 is Now Available


